Removing Entries from an ARP Table (24.1.6)
For each device, an ARP cache timer removes ARP entries that have not been used for a specified period of time. The times differ depending on the operating system of the device. For example, newer Windows operating systems store ARP table entries between 15 and 45 seconds, as illustrated in the Figure 24-4.
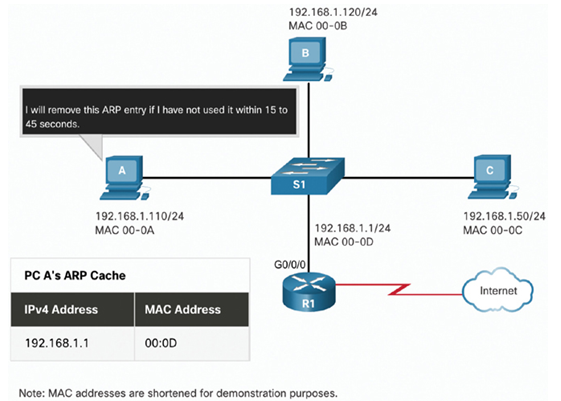
Figure 24-4 Removing MAC-to-IP Address Mappings
Commands may also be used to manually remove some or all of the entries in the ARP table. After an entry has been removed, the process for sending an ARP request and receiving an ARP reply must occur again to enter the map in the ARP table.
ARP Tables on Devices (24.1.7)
On a Cisco router, the show ip arp command is used to display the ARP table, as shown Example 24-1.
R1#
show ip arp
Protocol Address Age (min) Hardware Addr Type Interface
Internet 192.168.10.1 – a0e0.af0d.e140 ARPA GigabitEthernet0/0/0
Internet 209.165.200.225 – a0e0.af0d.e141 ARPA GigabitEthernet0/0/1
Internet 209.165.200.226 1 a03d.6fe1.9d91 ARPA GigabitEthernet0/0/1
R1#
On a Windows 10 PC, the arp –a command is used to display the ARP table, as shown in Example 24-2.
Example 24-2 Windows 10 PC ARP Table
C:\Users\PC>
arp -a
Interface: 192.168.1.124 — 0x10
Internet Address Physical Address Type
192.168.1.1 c8-d7-19-cc-a0-86 dynamic
192.168.1.101 08-3e-0c-f5-f7-77 dynamic
192.168.1.110 08-3e-0c-f5-f7-56 dynamic
192.168.1.112 ac-b3-13-4a-bd-d0 dynamic
192.168.1.117 08-3e-0c-f5-f7-5c dynamic
192.168.1.126 24-77-03-45-5d-c4 dynamic
192.168.1.146 94-57-a5-0c-5b-02 dynamic
192.168.1.255 ff-ff-ff-ff-ff-ff static
224.0.0.22 01-00-5e-00-00-16 static
224.0.0.251 01-00-5e-00-00-fb static
239.255.255.250 01-00-5e-7f-ff-fa static
255.255.255.255 ff-ff-ff-ff-ff-ff static
C:\Users\PC>
ARP Issues – ARP Broadcasts and ARP Spoofing (24.1.8)
As a broadcast frame, an ARP request is received and processed by every device on the local network. On a typical business network, these broadcasts would probably have minimal impact on network performance. However, if a large number of devices were to be powered up and all start accessing network services at the same time, there could be some reduction in performance for a short period of time, as shown in Figure 24-5. After the devices send out the initial ARP broadcasts and have learned the necessary MAC addresses, any impact on the network will be minimized.
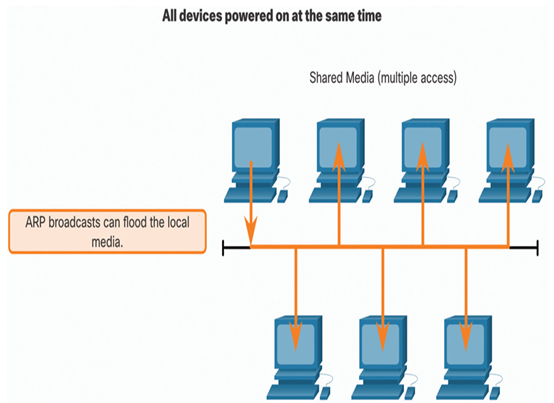
Figure 24-5 ARP Broadcasts Flooding a Network
In some cases, the use of ARP can lead to a potential security risk. A threat actor can use ARP spoofing to perform an ARP poisoning attack. This is a technique used by a threat actor to reply to an ARP request for an IPv4 address that belongs to another device, such as the default gateway, as shown in Figure 24-6. The threat actor sends an ARP reply with its own MAC address. The receiver of the ARP reply will add the wrong MAC address to its ARP table and send these packets to the threat actor.

Figure 24-6 Threat Actor Spoofing an ARP Reply
Enterprise level switches include mitigation techniques known as dynamic ARP inspection (DAI). DAI is beyond the scope of this course.
Packet Tracer – Examine the ARP Table (24.1.9)
In this Packet Tracer, activity you will complete the following objectives:
• Examine an ARP Request
• Examine a Switch MAC Address Table
• Examine the ARP Process in Remote Communications
This activity is optimized for viewing PDUs. The devices are already configured. You will gather PDU information in simulation mode and answer a series of questions about the data you collect.
Refer to the online course to complete this activity.
Lab – View ARP Traffic in Wireshark (24.1.10)
In this activity, you will complete the following objectives:
Part 1: Capture and Analyze ARP Data in Wireshark
Part 2: View the ARP cache entries on the PC
Refer to the online course to complete this lab.
