Syntax Checker – Configure Initial Router Settings (28.2.3)
Use this syntax checker to practice configuring the initial settings on a router.
- Configure the device name.
- Secure the privileged EXEC mode.
- Secure and enable remote SSH and Telnet access.
- Secure all plaintext passwords.
- Provide legal notification.
Refer to the online course to complete this Activity.
Packet Tracer – Configure Initial Router Settings (28.2.4)
In this activity, you will complete the following objectives:
- Verify the Default Router Configuration
- Configure and Verify the Initial Router Configuration
- Save the Running Configuration File
Refer to the online course to complete this Activity.
Secure the Devices (28.3)
Properly securing a device should always be done before putting the device into the production network.
Password Recommendations (28.3.1)
To protect network devices, it is important to use strong passwords. Here are standard guidelines to follow:
- Use a password length of at least eight characters, preferably 10 or more characters. A longer password is a more secure password.
- Make passwords complex. Include a mix of uppercase and lowercase letters, numbers, symbols, and spaces, if allowed.
- Avoid passwords based on repetition, common dictionary words, letter or number sequences, usernames, relative or pet names, biographical information, such as birthdates, ID numbers, ancestor names, or other easily identifiable pieces of information.
- Deliberately misspell a password. For example, Smith = Smyth = 5mYth or Security = 5ecur1ty.
- Change passwords often. If a password is unknowingly compromised, the window of opportunity for the threat actor to use the password is limited.
- Do not write passwords down and leave them in obvious places such as on the desk or monitor.
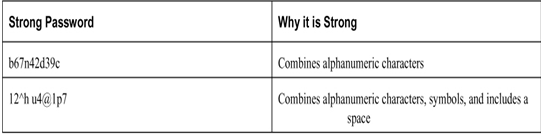
Tables 28-1 and 28-2 show examples of strong and weak passwords.
Table 28-1 Weak Password Examples

Table 28-2 Strong Password Examples
On Cisco routers, leading spaces are ignored for passwords, but spaces after the first character are not. Therefore, one method to create a strong password is to use the space bar and create a phrase made of many words. This is called a passphrase. A passphrase is often easier to remember than a simple password. It is also longer and harder to guess.
Secure Remote Access (28.3.2)
There are multiple ways to access a device to perform configuration tasks. One of these ways is to use a PC attached to the console port on the device. This type of connection is frequently used for initial device configuration.
Setting a password for console connection access is done in global configuration mode. These commands prevent unauthorized users from accessing user mode from the console port.
Switch(config)#
line console 0
Switch(config)#
password
password
Switch(config)#
login
When the device is connected to the network, it can be accessed over the network connection using SSH or Telnet. SSH is the preferred method because it is more secure. When the device is accessed through the network, it is considered a vty connection. The password must be assigned to the vty port. The following configuration is used to enable SSH access to the switch.
Switch(config)#
line vty 0 15
Switch(config)#
password
password
Switch(config)#
transport input ssh
Switch(config)#
login
Example 28-7 shows a sample configuration.
Example 28-7 Secure Remote Access with Passwords
S1(config)#
line console 0
S1(config-line)#
password cisco
S1(config-line)#
login
S1(config-line)#
exit
S1(config)#
S1(config)#
line vty 0 15
S1(config-line)#
password cisco
S1(config-line)#
login
S1(config-line)#
By default, many Cisco switches support up to 16 vty lines that are numbered 0 to 15. The number of vty lines supported on a Cisco router varies with the type of router and the IOS version. However, five is the most common number of vty lines configured on a router. These lines are numbered 0 to 4 by default, though additional lines can be configured. A password needs to be set for all available vty lines. The same password can be set for all connections.
To verify that the passwords are set correctly, use the show running-config command. These passwords are stored in the running-configuration in plaintext. It is possible to set encryption on all passwords stored within the router so that they are not easily read by unauthorized individuals. The global configuration command service password-encryption ensures that all passwords are encrypted.
With remote access secured on the switch, you can now configure SSH.
