802.11 Original Authentication Methods (39.6.9)
Although SSID cloaking and MAC address filtering would deter most users, the reality is that neither feature would deter a crafty intruder. SSIDs are easily discovered even if APs do not broadcast them, and MAC addresses can be spoofed. The best way to secure a wireless network is to use authentication and encryption systems.
Two types of authentication were introduced with the original 802.11 standard:
• Open system authentication—Any wireless client will easily be able to connect. Open system authentication should only be used in situations where security is of no concern, such as those providing free Internet access like cafes, hotels, and in remote areas. The wireless client is responsible for providing security, such as by using a virtual private network (VPN) to connect securely. VPNs provide authentication and encryption services. VPNs are beyond the scope of this topic.
• Shared key authentication—This provides mechanisms such as WEP, WPA, WPA2, and WPA3 to authenticate and encrypt data between a wireless client and AP. However, the password must be pre-shared between both parties to connect.
The chart in Figure 39-27 summarizes these authentication methods.
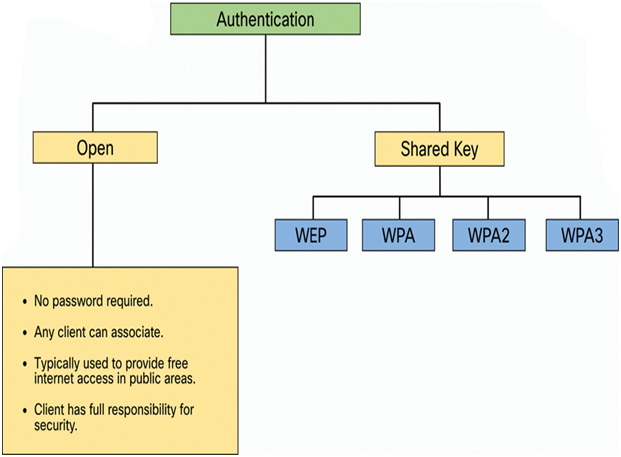
Figure 39-27 802.11 Authentication Methods
(e)Shared Key Authentication Methods (39.6.10)
There are four shared key authentication techniques available, as described in Table 39-7. Until the availability of WPA3 devices becomes ubiquitous, wireless networks should use the WPA2 standard.
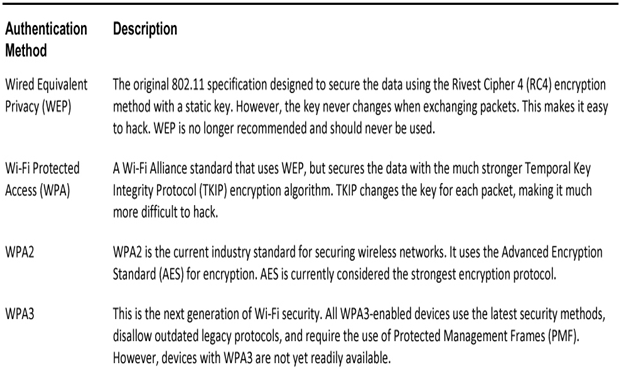
Table 39-7 802.11 Shared Key Authentication Techniques
Authenticating a Home User (39.6.11)
Home routers typically have two choices for authentication: WPA and WPA2. WPA2 is the stronger of the two. Figure 39-28 shows the option to select one of two WPA2 authentication methods:
- Personal—Intended for home or small office networks, users authenticate using a pre-shared key (PSK). Wireless clients authenticate with the wireless router using a pre-shared password. No special authentication server is required.
- Enterprise—Intended for enterprise networks but requires a Remote Authentication Dial-In User Service (RADIUS) authentication server. Although more complicated to set up, it provides additional security. The device must be authenticated by the RADIUS server and then users must authenticate using the 802.1X standard, which uses the Extensible Authentication Protocol (EAP) for authentication.
In Figure 39-28, the administrator is configuring the wireless router with WPA2-Personal authentication on the 2.4 GHz band.
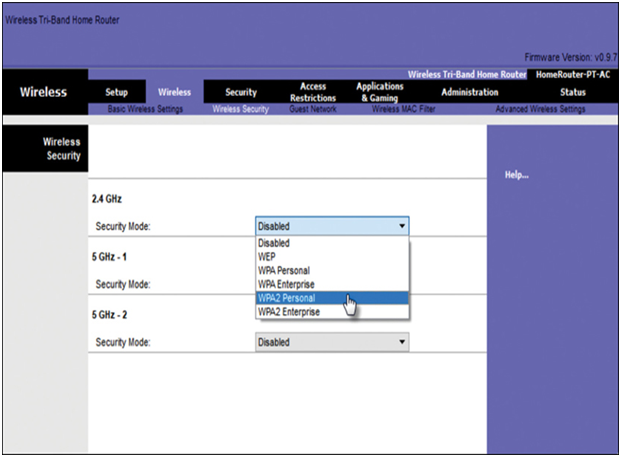
Figure 39-28 Example of Configuring WPA2-Personal Authentication
Encryption is used to protect data. If an intruder has captured encrypted data, they would not be able to decipher it in any reasonable amount of time.
The WPA and WPA2 standards use the following encryption protocols:
- Temporal Key Integrity Protocol (TKIP)—TKIP is the encryption method used by WPA. It provides support for legacy WLAN equipment by addressing the original flaws associated with the 802.11 WEP encryption method. It makes use of WEP, but encrypts the Layer 2 payload using TKIP, and carries out a Message Integrity Check (MIC) in the encrypted packet to ensure the message has not been altered.
- Advanced Encryption Standard (AES)—AES is the encryption method used by WPA2. It is the preferred method because it is a far stronger method of encryption. It uses the Counter Cipher Mode with Block Chaining Message Authentication Code Protocol (CCMP) that allows destination hosts to recognize if the encrypted and non-encrypted bits have been altered.
In Figure 39-29, the administrator is configuring the wireless router to use WPA2 with AES encryption on the 2.4 GHz band.
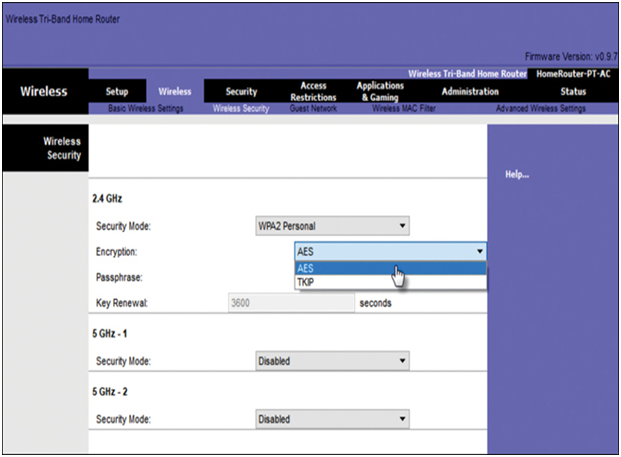
Figure 39-29 Example of Configuring AES Encryption for WPA2
