Management groups can also be used to apply Azure RBAC to a subscription. Using man- agement groups, you can apply governance consistently across subscriptions, including the application of common RBAC controls and the application of Azure Policy, as discussed later in this chapter.
Within management groups, subscriptions can be organized in a multi level hierarchy,
providing a number of tangible benefits:
- Reduced overhead There is no need to apply governance on every subscription.
- Enforcement Company admins can apply governance at the management group level, outside the control of the subscription admin and the controls implemented at the management group can be applied to both existing and new subscriptions. This elimi- nates inconsistencies in the application of governance as the same controls are applied the same way to the desired subscriptions.
- Reporting Azure Policy provides reports of compliance. With management groups, the reporting can span across multiple or all subscriptions in an organization.
Management groups form a hierarchy that is up to six levels deep, excluding the root and subscription levels. Each group has exactly one parent and can have multiple children. An example hierarchy is shown in Figure 1-52. In such a hierarchy, one common set of Policy could be applied at the root management group, which all child management groups and subscriptions would inherit. Then, as needed, those children can have additional controls applied
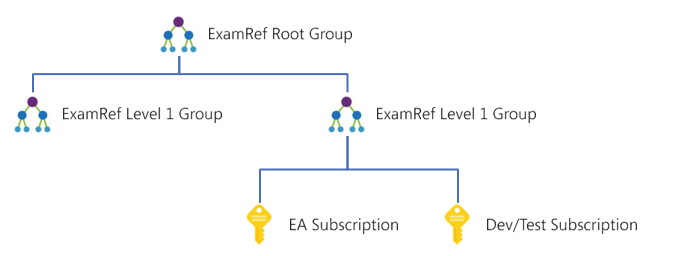
FIGURE 1-52 Example management group hierarchy
There is a single root management group at the root of the hierarchy. This management group is associated with the Entra tenant that is then associated with an Azure subscription. It cannot be moved or deleted. Individual subscriptions, including new subscriptions, are added to a management group.
Like RBAC, Azure Policy is also applied at a specific scope. The scope can be a subscription, a resource group, or an individual resource. For example, when a policy is applied at the sub- scription scope, it is inherited by all the resource groups and resources in the subscription, as shown in Figure 1-53.
Management groups introduce an additional scope above a subscription. When applied at the management group scope, each subscription under the management group inherits the RBAC and policy assignments of the management group as shown in Figure 1-54.
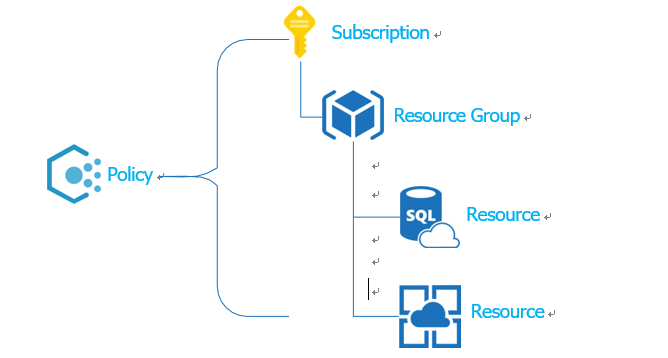
FIGURE 1-53 Example policy applied at the subscription scope
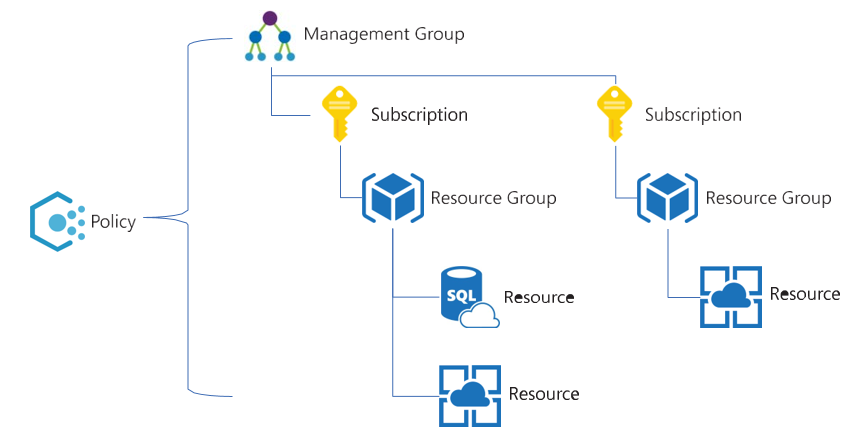
FIGURE 1-54 Example policy applied at the management group scope
To add a role assignment to a management group, browse to management groups in the Azure portal. Select a management group and then click Details next to that group’s name. Select the Access Control (IAM) blade, click Add, and choose Add Role Assignment, just as you would for an Azure subscription, as shown in Figure 1-55.
FIGURE 1-55 Access control (IAM) blade for an Azure management group

