In the previous chapters, topics such as roles, users, and service accounts often appeared in the context of what permissions are needed to access or configure a specific Google Cloud service. This chapter will provide more visibility on identity and access in Google Cloud. In addition, we will focus on the security aspter and learn about preventing unauthorized access and auditing user actions on Google Cloud resources.
Furthermore, the Google Cloud setup checklist section in Chapter 3 briefly mentioned a checklist that guided users through the initial setup of Google Cloud foundation in order to run enterprise ready workloads.The first points on this list were Cloud Identity users and groups, and administrative access. As those topics are important from the identity and security perspective, we will cover them in detail.
In this chapter, we will explore the following main topics:
- Creating a cloud identity for an organization
- Providing access to Google Cloud resources
- Managing service accounts
- Using Cloud Audit Logs for security and compliance
Suppose you use a Google Cloud free trial, as described in the Billing and budgets section in Chapter 3, to learn about the platform or use Google Cloud for small personal projects. To keep things simple, as you are the only user, you probably use your @gmail account, assigning it a Project Owner role for every project you create. The following figure shows an example of such a configuration:
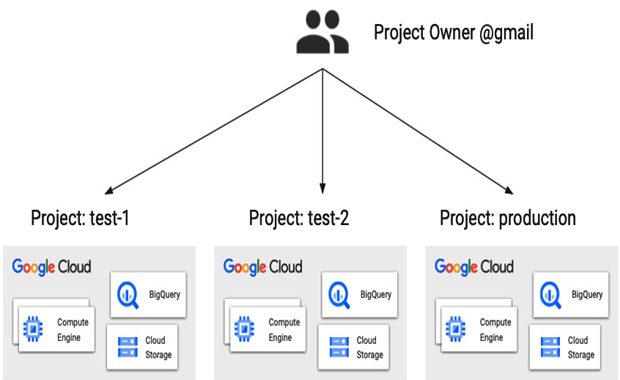
Figure 12.1 – Multiple personal projects owned by a single user
This approach is a good fit for small projects owned by a single user or just a few users, but a more scalable solution is needed for an enterprise. First, to manage access for multiple users and groups, and second, to provide a hierarchy of resources to match a large organization’s structure – departments, teams, or applications. This is where Google’s identity service comes into play as an alternative to using individual @gmail.com accounts.
Google’s Identity as a Service platform allows for centralized management of users and groups. The platform includes security features such as password management, two-step verification, and single sign-on for SAML applications or third-party identity providers. Additionally, there is an option to synchronize identities from Active Directory or OpenLDAP to a Google directory.
There are two ways to configure an identity:
- Cloud Identity, which is available in both free and premium versions
- Workspace, which includes extra services such as Gmail, Google Drive, Docs, and Sheets
A company using a different identity provider still needs an identity account in Cloud Identity or Workspace. However, they can federate their provider to their Google identity account to access Google Cloud with existing credentials.
Let’s look at the example process of creating a free Cloud Identity account. To start the configuration, a company needs a domain. If it doesn’t own a domain, one can be purchased at https://domains.google.com, as presented in the following figure:
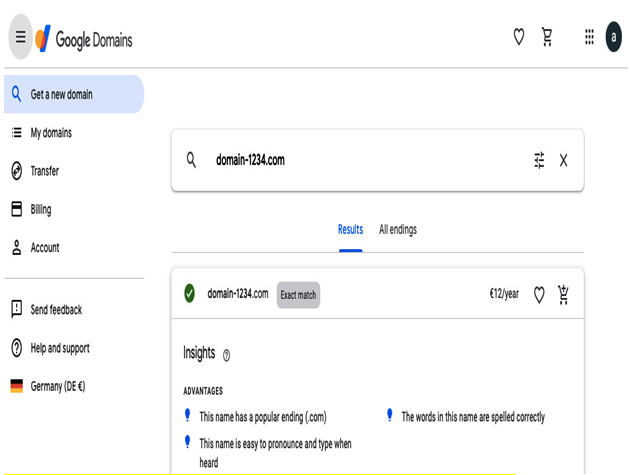
Figure 12.2 – Google Domains portal, where you can purchase and manage domains
Note that a domain doesn’t necessarily have to come from the Google Domains platform. Next, a domain will be used to set up Cloud Identity. One domain can be associated with only one Cloud Identity
If logged in to the Google Cloud console as a @gmail user, you can set up your organization and Cloud Identity in the Identity & Organization section of IAM & Admin, as shown in the following screenshot:
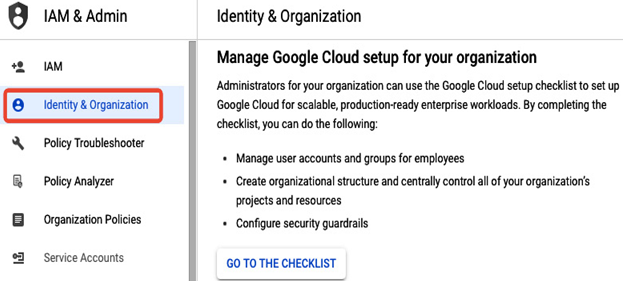
Figure 12.3 – Set up a Google Cloud organization in the console
If you select GO TO THE CHECKLIST, you will directly access the Cloud Identity setup from the Google Cloud console:
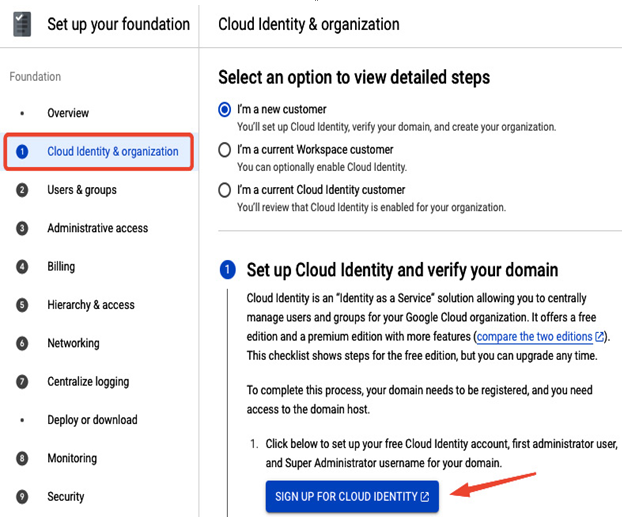
Figure 12.4 – Setup of Cloud Identity in the Google Cloud console
Alternatively, if you haven’t logged in to the Google Cloud console before but you own a domain, you can start setting up Cloud Identity using the following link: https://workspace.google.com/gcpidentity/signup/welcome?sku=identitybasic.
During the Cloud Identity setup, you provide a company name, contact info with an email from a different domain that will be used as a recovery email, a new or existing domain, and login details. A user created during the identity setup will have a Super Admin role, which is an administrator seed role with all permissions:
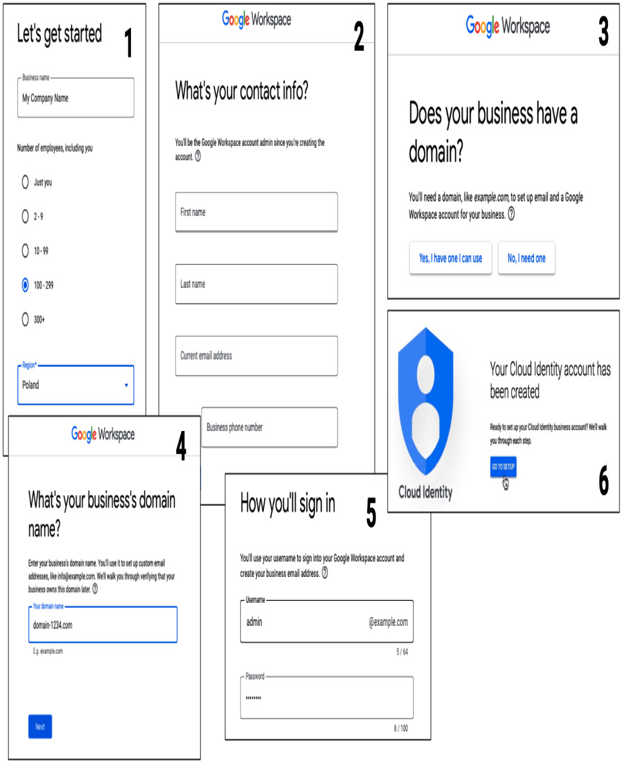
Figure 12.5 – Selected screenshots from initializing Cloud Identity for a domain
Once the setup is done, you can further configure your Cloud Identity in the Google Admin console at https://admin.google.com using a new administrator account. Note that this is a different portal from the Google Cloud console.
Before you start creating users, Google must verify your domain ownership. For that reason, you will be asked to add a new TXT record to your domain on your host’s website:
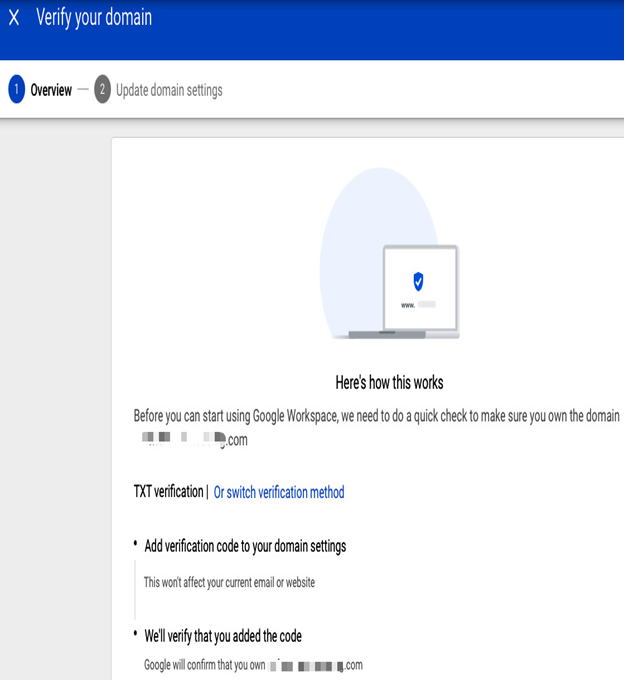
Figure 12.6 – Domain verification for Cloud Identity
Google recommends using a super admin account only when necessary; for example, for account recovery scenarios. For day-to-day activities, separate accounts with fewer permissions should be created. Once your domain is configured and verified, you can proceed with creating users that will access Google Cloud resources.
