A service account is an identity that an application or a Compute Engine VM uses to run authorized API calls to Google Cloud services such as Google Cloud Storage, BigQuery, and so on. Contrary to a user account, this account type is not created in the Google Admin console as a Cloud Identity, but in a Google Cloud project. It doesn’t have a password and can’t be used for interactive login to a console. Service accounts can be used by applications running in Google Cloud and on-premises. Also, users can use service accounts in certain scenarios.
There are the following types of service accounts:
- Google-managed service accounts (service agents) are created automatically so that Google Cloud services that you enable can interact with your resources. You can find the complete list of service agents at https://cloud.google.com/iam/docs/service-agents.
- User-managed default service accounts are created automatically when an API for a service is enabled. They help to get started with a service but can be modified or replaced later. For example, Compute Engine comes with a default service account: <project-number>[email protected].
- User-managed service accounts are created in IAM by a user with permissions: iam.serviceAccounts.create. A predefined role, Service Account Admin, or Create Service Accounts can be used for this task. User-defined accounts use the following format: <service-account-name>@project-id.iam.gserviceaccount.com.
Service accounts authenticate via short-lived credentials or associated public/private RSA key pairs.
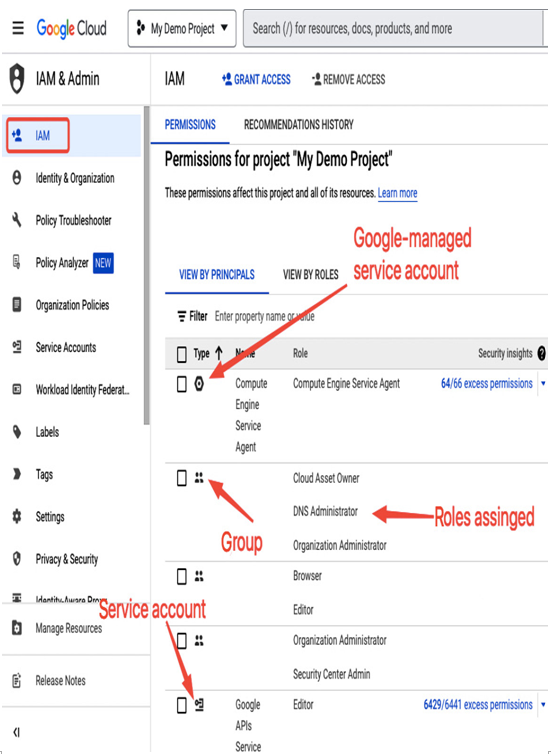
Figure 12.30 – Users, groups, and service accounts listed in the IAM section
You can view the list of service accounts in the IAM section, as shown in the preceding screenshot. Alternatively, you can use the gcloud command:
gcloud iam service-accounts list
Now, having introduced the concept of a service account, in the next section, we will look into how to create and manage permissions for this type of account.
Creating and granting permissions
As service accounts are not a part of Cloud Identity, there is a dedicated section, Service accounts in the IAM & Admin view, where you can create and configure them. For example, the following screenshot presents a service account created in the console:
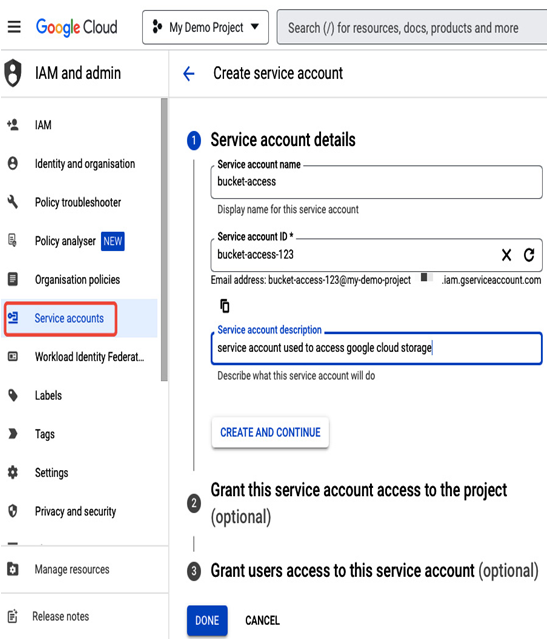
Figure 12.31 – Creating a service account in the Google Cloud console
After selecting CREATE SERVICE ACCOUNT in the Service accounts section, you need to provide a descriptive name, such as bucket-access in this example, and either add roles and users that can impersonate the account or skip this step and assign them later. The gcloud command equivalent would be the following:
gcloud iam service-accounts create bucket-access –description=”account used to access google cloud storage” –display-name=”bucket-access”
For the role assignments for a service account, go to the IAM section and select GRANT ACCESS, as presented in the following figure. Provide your service account in the Add principals section and select required roles in the Assign roles section. Role assignment for service accounts is similar to user role assignment. Using service accounts with minimum permissions is recommended, so even though it is possible to assign basic roles to a service account, it would be better to use predefined or customized roles.
In the example that follows, a bucket-access service account is granted the Storage Admin role. This means that whoever has access to this account (a user, a Compute Engine VM, or a service) can use it to interact with Google Cloud Storage to create or delete buckets and objects:
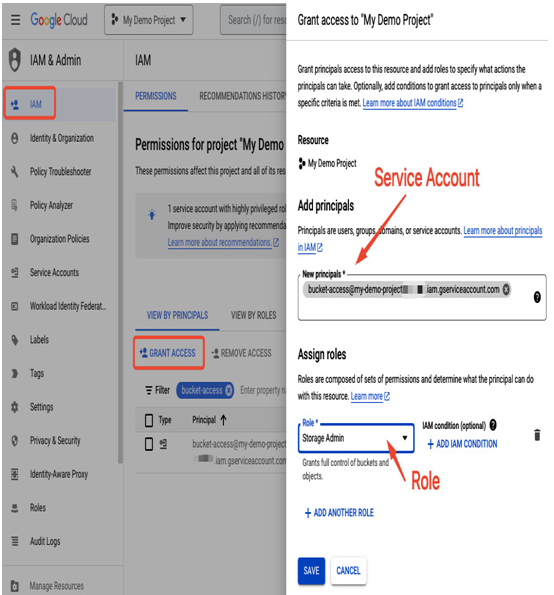
Figure 12.32 – Assigning a role to a service account
Users that use basic roles have access to service accounts by default. If you don’t use basic roles, you need to explicitly grant a user access to a service account in the Service Accounts view by selecting a service account and then selecting GRANT ACCESS in the PERMISSIONS tab:
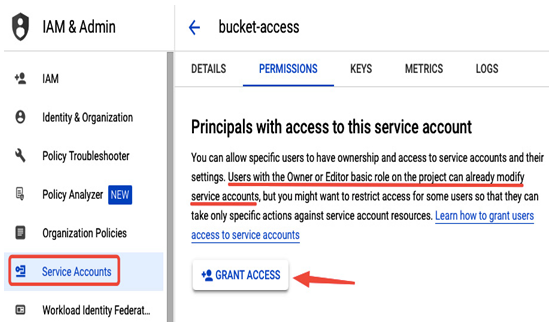
Figure 12.33 – Granting access to a service account for a user
By granting access, you use a service account not as an account anymore. It becomes a resource, meaning you grant a user a specific role on a service account. For example, when you create a Compute Engine VM, you can provide a service account that this VM will use to access services such as Google Cloud Storage.
Note that if you don’t have a Service Account User role on this service account, you won’t be able to create a VM with this service account assigned.
