To securely communicate and share resources over a network that is not secure, such as the Internet, a Virtual Private Network (VPN) is used. The most common types of VPN are used to access a corporate private network either by remote users or by remote corporate sites.
A VPN uses dedicated secure connections, routed through the Internet, from the corporate private network to the remote user. When connected to the corporate private network, remote-access VPN users become part of that network and have access to all services and resources as if they were physically connected to it. VPNs are also used to connect branch offices and other facilities to the corporate network.
VPNs are commonly deployed in one of the following configurations: site-to-site or remote-access.
A site-to-site VPN is created when VPN terminating devices, also called VPN gateways, are preconfigured with information to establish a secure tunnel, as shown in Figure 37-41. VPN traffic is only encrypted between these devices. Internal hosts have no knowledge that a VPN is being used.
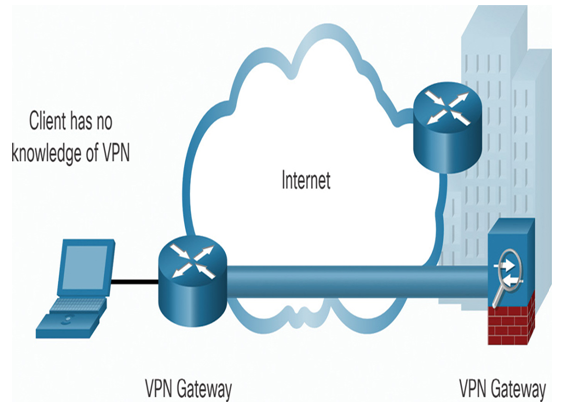
Figure 37-41 An Example of Site-to-Site VPN
A remote-access VPN is dynamically created to establish a secure connection between a client and a VPN terminating device, as shown in Figure 37-42. For example, a remote-access SSL VPN is used when you check your banking information online.
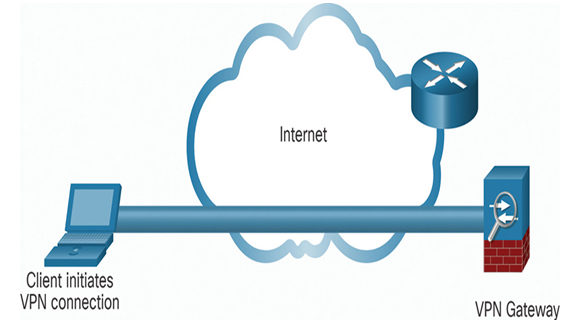
Figure 37-42 An Example of Remote-Access VPN
Remote-access users must install a VPN client on their computers to form a secure connection with the corporate private network. Special routers can also be used to connect computers to the corporate private network. The VPN software encrypts data before sending it over the Internet to the VPN gateway at the corporate private network. VPN gateways establish, manage, and control VPN connections, also known as VPN tunnels. Windows supports several VPN types; however, for some VPNs, third-party software may be required. The Cisco AnyConnect VPN client is shown in Figure 37-43.
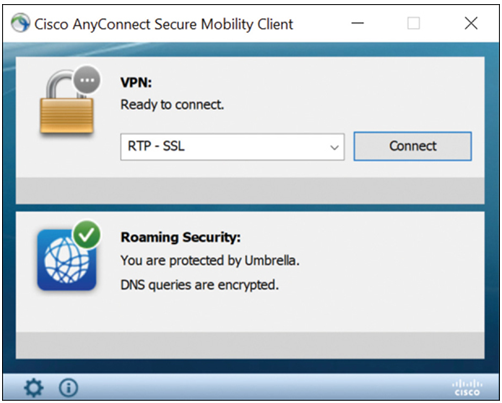
Figure 37-43 Cisco AnyConnect Secure Mobility Client
A VPN in Windows 10 can be set up from Network & Internet settings as shown in Figure 37-44.
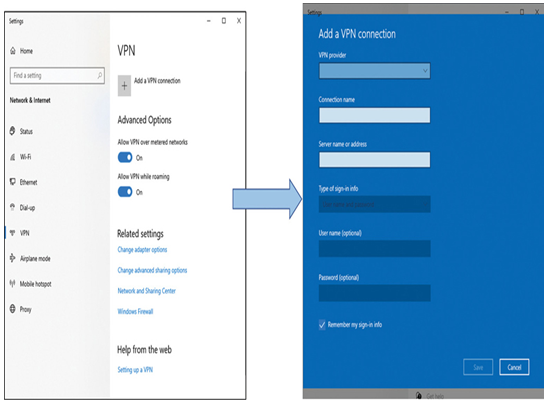
Figure 37-44 Windows 10 VPN Configuration
In addition to securing remote desktop sharing for technical support purposes, users can use remote desktop to remotely access computers within the corporate network in order to carry out their normal work duties. This means that a user can access the desktop of their work computer from their home computer. This permits workers to access work resources from their own devices and access files and programs hosted by their work PC remotely. In addition, computing with cloud-based virtual desktops is becoming popular. Organizations can save money and create efficiencies by outsourcing management of workstations to the cloud. In this case, user workstations are cloud-hosted virtual machines. This permits users to access their computer resources from virtually any device that supports a compatible remote desktop client.
This can create security challenges, however. Many remote desktop clients are not secure. Using VPNs to access remote and cloud-based virtual computer workstations ensures greater security when this solution is in use. Microsoft Azure and Amazon Web Services provide remote workspace solutions. IT support personnel will be required to help workers access and operate these virtual resources.
