Deception (38.2)
Deception comes in many forms. This section explores some of the different ways attackers can attempt to deceive a person or organization.
Social Engineering (38.2.1)
Social engineering is a non-technical strategy that attempts to manipulate individuals into performing risky actions or divulging confidential information.
Rather than software or hardware vulnerabilities, social engineering exploits human nature by taking advantage of people’s willingness to help or preying on their weaknesses, such as greed or vanity.
The following are some common types of social engineering.
Pretexting
This type of attack occurs when an individual lies to gain access to privileged data. For example, an attacker pretends to need personal or financial data in order to confirm a person’s identity.
Something for Something (Quid Pro Quo)
Quid pro quo attacks involve a request for personal information in exchange for something, like a gift. For example, a malicious email could ask you to give your sensitive personal details in exchange for a free vacation.
Identity Fraud
This is the use of a person’s stolen identity to obtain goods or services by deception. For example, someone acquires your personal information and attempts to apply for a credit card in your name.
Social Engineering Tactics (38.2.2)
Cybercriminals rely on several social engineering tactics, as shown in Table 38-3, to gain access to sensitive information.
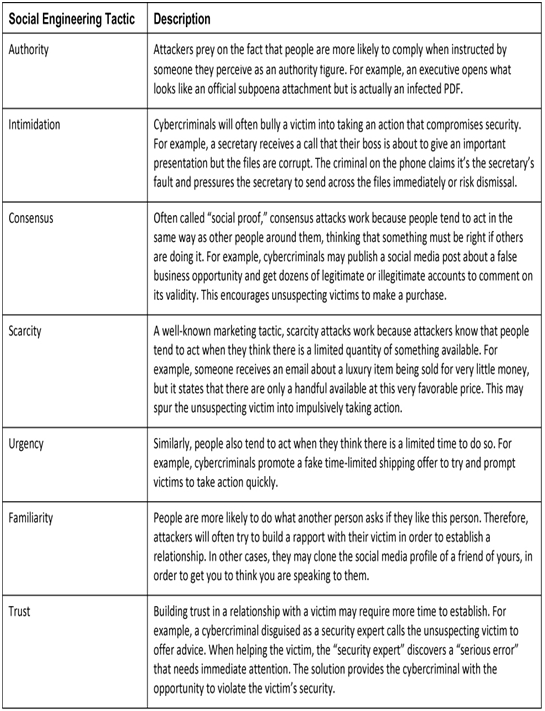
Table 38-3 Social Engineering Tactics
Practice Item—Social Engineering Scenario (38.2.3)
Refer to the online course to complete this activity.
Shoulder Surfing and Dumpster Diving (38.2.4)
Shoulder surfing is a simple attack that involves observing or literally looking over a target’s shoulder to gain valuable information such as PINs, access codes, or credit card details. Criminals do not always have to be near their victim to shoulder surf. They can use binoculars or security cameras to obtain this information.
This is one reason why an ATM screen can only be viewed at certain angles. These types of safeguards make shoulder surfing much more difficult.
You might have heard of the phrase, “one man’s trash is another man’s treasure.” Nowhere is this more true than in the world of dumpster diving, which is the process of going through a target’s trash to see what information has been thrown out.
This is why documents containing sensitive information should be shredded or stored in burn bags until they can be destroyed.
Impersonation and Hoaxes (38.2.5)
Cybercriminals have many other deception techniques to help them succeed.
Impersonation is the act of pretending to be someone else to trick someone into doing something they would not ordinarily do. For example, a cybercriminal posing as an IRS employee recently targeted taxpayers, telling the victims that they owed money that had to be paid immediately via wire transfer—or risk arrest.
Criminals can also use impersonation to attack others. For example, they can pose as their victim online and post on websites or social media pages to undermine the victim’s credibility.
A hoax is an act intended to deceive or trick someone. Hoaxes can cause just as much disruption as an actual security breach.
For example, a message warns of a (nonexistent) virus threat on a device and asks the recipient to share this information with everyone they know. This hoax elicits a user reaction, creating fear and irrational behavior that is propagated through email and social media.
