Piggybacking and Tailgating (38.2.6)
Piggybacking or tailgating occurs when a criminal follows an authorized person to gain physical entry into a secure location or a restricted area. Criminals can achieve this by:
- Giving the appearance of being escorted into the facility by an authorized person
- Joining and pretending to be part of a large crowd that enters the facility
- Targeting an authorized person who is careless about the rules of the facility
One way of preventing this is to use two sets of doors. This is sometimes referred to as a mantrap and means individuals enter through an outer door, which must close before they can gain access through an inner door.
Other Methods of Deception (38.2.7)
Be aware that attackers have many more tricks up their sleeve to deceive their victims. Table 38-4 list some addition methods of deception.
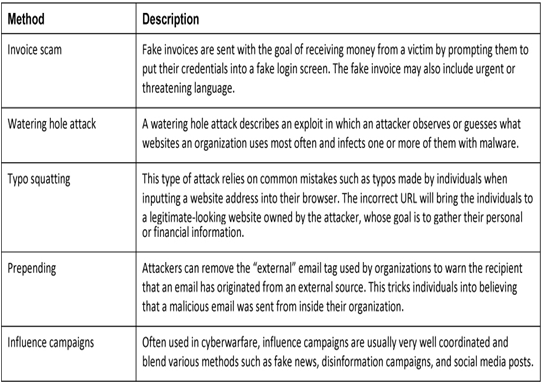
Table 38-4 Other Methods of Deception
Check Your Understanding—Social Engineering Attacks (38.2.8)
Refer to the online course to complete this activity.
Defending Against Deception (38.2.9)
Organizations need to promote awareness of social engineering tactics and properly educate employees on prevention measures. Here are some top tips:
- Never disclose confidential information or credentials to unknown parties via email, chat, text messages, or in conversation.
- Resist the urge to click on enticing emails and web links.
- Be wary of uninitiated or automatic downloads.
- Establish and educate employees on key security policies.
- Encourage employees to take ownership of security issues.
- Do not give in to pressure by unknown individuals.
Video—Explore Social Engineering Techniques (38.2.10)
Refer to the online course to view this video.
Lab—Explore Social Engineering Techniques (38.2.11)
In this lab, you will complete the following objectives:
- Part 1: Explore Social Engineering Techniques
- Part 2: Create a Cybersecurity Awareness Poster
Refer to the online course to complete this lab.
Cyber Attacks (38.3)
There are many different types of cyber attacks that can target the end devices or the entire network. This section explores some of the most common cyber attacks.
Malware (38.3.1)
Cybercriminals use many different types of malicious software, or malware, to carry out attacks. Malware is any code that can be used to steal data, bypass access controls or cause harm to or compromise a system.
Viruses
A virus is a type of computer program that, when executed, replicates and attaches itself to other files, such as legitimate programs, by inserting its own code into the file. Some viruses are harmless yet others can be destructive, such as those that modify or delete data. Most viruses require end-user interaction to initiate activation, and can be written to act on a specific date or time.
Viruses can be spread through removable media such as USB flash drives, Internet downloads, and email attachments. The simple act of opening a file or executing an infected program can trigger a virus. Once a virus is active, it will usually infect other programs on the computer or other computers on the network. Viruses mutate to avoid detection.
For example, the Melissa virus was released in 1999 and spread via email, affecting tens of thousands of users and causing an estimated $1.2 billion in damage.
Worms
A worm is a malicious software program that replicates by independently exploiting vulnerabilities in networks. Unlike a virus, which requires a host program to run, worms can run by themselves. Other than the initial infection of the host, they do not require user participation and can spread very quickly over the network, usually slowing it down.
Worms share similar patterns: they exploit system vulnerabilities, they have a way to propagate themselves, and they all contain malicious code (payload) that causes damage to computer systems or networks.
Worms are responsible for some of the most devastating attacks on the Internet. In 2001, the Code Red worm infected over 300,000 servers in just 19 hours.
Trojan Horse
A Trojan horse is malware that carries out malicious operations by masking its true intent. It might appear legitimate but is, in fact, very dangerous. Trojans exploit the privileges of the user who runs them.
Unlike viruses, Trojans do not self-replicate but often bind themselves to non-executable files, such as image, audio, or video files, that act as a decoy to harm the systems of unsuspecting users.
