Buffers are memory areas allocated to an application. A buffer overflow occurs when data is written beyond the limits of a buffer. By changing data beyond the boundaries of a buffer, the application can access memory allocated to other processes. This can lead to a system crash or data compromise, or provide escalation of privileges.
These memory flaws can also give attackers complete control over a target’s device. For example, an attacker can change the instructions of a vulnerable application while the program is loading in memory and, as a result, can install malware and access the internal network from the infected device.
Remote Code Executions (38.5.4)
Remote code execution allows a cybercriminal to take advantage of application vulnerabilities to execute any command with the privileges of the user running the application on the target device.
Privilege escalation exploits a bug, design flaw, or misconfiguration in an operating system or application to gain access to resources that are normally restricted.
The Metasploit Project is a computer security project that provides information about security vulnerabilities and aids in penetration testing. Among the tools they have developed is the Metasploit Framework, which can be used for developing and executing exploit code against a remote target.
Meterpreter, in particular, is a payload within Metasploit that allows users to take control of a target’s device by writing their own extensions and uploading these files into a running process on the device. These files are loaded and executed from memory, so they never involve the hard drive. This means that such files fly under the radar of antivirus detection.
Meterpreter also has a module for controlling a remote system’s webcam. Once Meterpreter is installed on a target device, the Metasploit user can view and capture images from the target’s webcam.
Other Application Attacks (38.5.5)
Every piece of information that an attacker receives about a targeted system or application can be used as a valuable weapon for launching a dangerous attack. Table 38-5 lists some other types of application attacks.
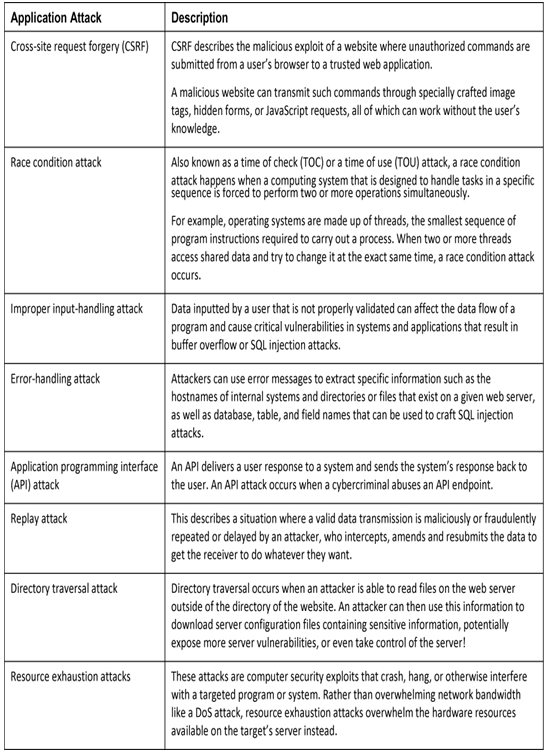
Table 38-5 Other Application Attacks
Practice Item—Code and Memory Attacks (38.5.6)
Refer to the online course to complete this activity.
Defending Against Application Attacks (38.5.7)
There are several actions that you can take to defend against an application attack. You will find some of them outlined here.
- The first line of defense against an application attack is to write solid code.
- Prudent programming practice involves treating and validating all input from outside of a function as if it is hostile.
- Use security testing tools to evaluate source code and binary software on an ongoing basis during the software development life cycle.
- Keep all software, including operating systems and applications, up to date and do not ignore update prompts. Remember that not all programs update automatically.
