The specific permissions that are applied to a resource with RBAC are defined in a role definition. A role definition contains the list of permissions—or declared permissions—and those permissions define what actions can or cannot be performed against a type of resource, such as read, write, or delete.
Role definitions, or roles, can be either built-in or custom. There are a number of built-in role definitions in Azure. An example of a built-in role is the Owner role, which includes permis- sions to manage resources, security, and the application of role assignments. Also, there are built-in roles with limited permission sets, such as a Storage Blob Data Reader, which allows the assigned security principal to only read and list containers and blobs.
There are many built-in roles in Azure, which can be found at https://docs.microsoft.com/ azure/role-based-access-control/built-in-roles. Microsoft adds new built-in roles as services evolve or as new services are introduced.
The access rights are controlled with a logical boundary known as scope. For example, to grant a user Contributor rights to all the resources in a resource group, the Contributor role can be assigned to the group at the resource group scope where it is then inherited by all of the resources in the resource group.
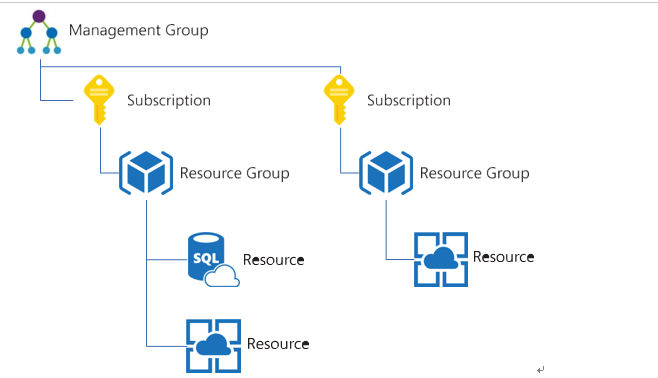
There are four scopes at which RBAC can be applied, and scopes are structured in a parent- child relationship where RBAC is inherited by any child scopes. The highest scope, or top-most parent scope, is a management group.
EXAM TIP
Management groups are not applicable in all scenarios, and in some cases, a subscription will be the highest scope you will work with when applying role assignments. This will be determined by your organization’s Azure landing zone deployment stamp.
Under the management group are more management groups and/or subscriptions; under subscriptions are resource groups; and under resource groups are resources. Figure 1-15 shows a sample hierarchy with a parent management group and two subscriptions, each with a resource group and child resources. Note that you can also create another management group under a root management group. An Entra ID tenant can support up to 10,000 management groups.

After you have identified the role, security principal, and scope at which the role will be assigned, you can make the assignment. Remember, security principals do not have access to Azure resources until a role assignment is made, and that access can be revoked by removing a role assignment.

To create and remove role assignments, you must have Microsoft.Authorization/role- Assignments/* permission at the necessary scope. This permission is granted through the Owner or User Access Administrator built-in roles, or it can be included in custom roles.

