Malware, is short for “malicious software.” Malware is any type of software that is specifically designed to damage, disrupt, or gain unauthorized access to end devices or networks. The intent of malware is to steal sensitive information, compromise system functionality, or perform other harmful actions
The term “endpoint” is defined in various ways. For the purpose of this course, we can define endpoints as hosts on the network that can access or be accessed by other hosts on the network. This obviously includes computers and servers, but many other devices can also access the network. With the rapid growth of the Internet of Things (IoT), other types of devices are now endpoints on the network. This includes networked security cameras, controllers, and even light bulbs and appliances. Each endpoint is potentially a way for malicious software to gain access to a network. In addition, new technologies, such as cloud, expand the boundaries of enterprise networks to include locations on the Internet for which enterprises are not responsible.
A recent survey of cybersecurity professionals asked the participants what security challenges they are most struggling with. As shown Figure 39-7, the top three are related to endpoint threats. Ransomware (53%) tops the list, following the recent rise in ransomware attacks. The next biggest security challenge is the shift to remote work and the resulting risks (47%), introduced in the wake of the Covid-19 pandemic. Limited visibility into cyber threats (41%) rounds out the top three security challenges experienced by cybersecurity professionals.
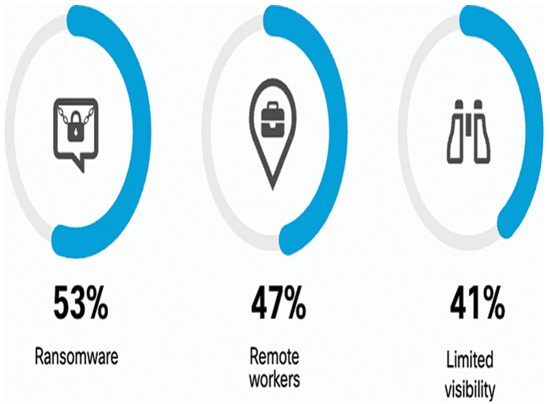
Figure 39-7 Survey—What Are Your Current Security Challenges?
Endpoint Security (39.4.2)
News media commonly cover external network attacks on enterprise networks. These are some examples of such attacks:
- DoS attacks on an organization’s network to degrade or even halt public access to it.
- Breach of an organization’s web server to deface their web presence.
- Breach of an organization’s data servers and hosts to steal confidential information.
Various network security devices are required to protect the network perimeter from outside access. As shown in Figure 39-8, these devices could include a hardened router that is providing VPN services, a next-generation firewall (ASA, in Figure 39-8), an IPS appliance, and an authentication, authorization, and accounting (AAA) services server (AAA Server, in Figure 39-8).
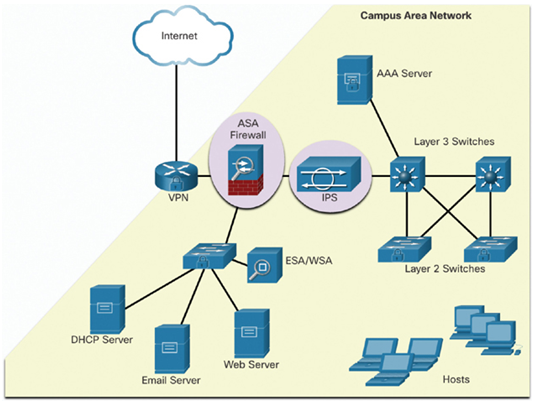
Figure 39-8 Example Topology of Security Devices in a Campus Network
However, many attacks originate from inside the network. Therefore, securing an internal LAN is nearly as important as securing the outside network perimeter. Without a secure LAN, users within an organization are still susceptible to network threats and outages that can directly affect the organization’s productivity and profit margin. After an internal host is infiltrated, it can become a starting point for an attacker to gain access to critical system devices, such as servers and sensitive information.
Specifically, there are two internal LAN elements to secure:
- Endpoints—Hosts commonly consist of laptops, desktops, printers, servers, and IP phones, all of which are susceptible to malware-related attacks.
- Network infrastructure—LAN infrastructure devices interconnect endpoints and typically include switches, wireless devices, and IP telephony devices. Most of these devices are susceptible to LAN-related attacks including MAC address table overflow attacks, spoofing attacks, DHCP-related attacks, LAN storm attacks, STP manipulation attacks, and VLAN attacks.
