Associate NSG to a subnet or network interface
NSGs are used to define the rules for how traffic is filtered for your IaaS deployments in Azure. You’ve learned how to create NSG resources and define the NSG rules. However, these NSGs, by themselves, are not effective until they are associated with a resource in Azure.
NSGs can be associated with network interface cards (NICs), which are associated to the VMs, or they can be associated with a subnet. Each NIC or subnet can only be associated with a single NSG. However, a single NSG can be associated with multiple NICs and/or subnets.
When an NSG is associated with a NIC, it applies to all IP configurations in that NIC. All inbound and outbound traffic to and from the NIC must be allowed by the NSG. It is possible to have a multi-NIC VM, and you can associate the same or different NSG to each network interface.
Alternatively, NSGs can be associated with a subnet; in that case, they apply to all traffic to and from resources in that subnet. This approach is useful when applying the same rule across multiple VMs.

You have seen how to create an NSG and how to add an inbound rule for HTTP and HTTPS traffic. Yet, unless the NSG has been associated with subnets or NICs, that rule is not in effect.
The next task will be to associate a rule with the Apps subnet. You can use either the NSG blade or the virtual network subnet blade for this task. This example uses the former.
In the NSG blade of the Azure portal, click Subnets to show the list of subnets currently associated with the NSG, which should be empty at this stage. Click Associate to open the Associate Subnet blade. The Azure portal will ask for two configurations: the virtual network, and the subnet. Note that you can only select virtual networks in the same Azure region as the NSG. In Figure 4-27, vnet-eastus-1 has been selected from the Virtual Network drop-down menu, and snet-eastus-1 has been selected from the Subnet drop-down menu.
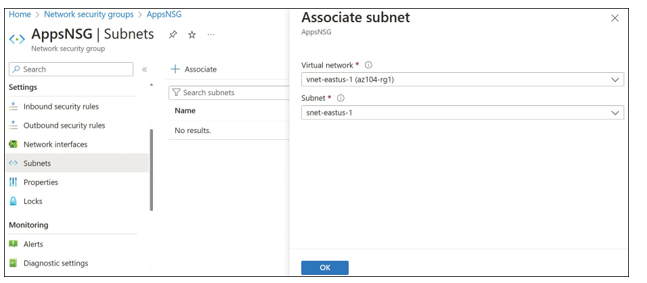
FIGURE 4-27 The ExamRef-VNet virtual network and Apps subnet have been selected
After you save them, the rules of the NSG are enforced for all network interfaces that are associated with this subnet. This will allow inbound TCP traffic on ports 80 and 443 for all VMs that are connected to this subnet. Of course, in order for it to respond, you need to have a webserver VM configured and listening on ports 80 or 443.
