Bastion hosts are VMs that provide secure access to other VMs in a GCP network. They should be hardened to be more secure than other VMs in the network. This includes using strong passwords and SSH keys, keeping the software up to date, and disabling unnecessary services. The idea is to restrict their access to your on-premises networks or specific narrowed-down network ranges.
Sometimes, bastion hosts are called jump boxes or jump servers. Regardless of the name, the idea is the same. They are secure and allow you to access your cloud infrastructure.
To learn more about bastion hosts and how to securely connect to the Google Cloud instances, visit the following link: https://cloud.google.com/solutions/connecting-securely.
Identity-Aware Proxy
Although Identity-Aware Proxy (IAP) isn’t a part of the Associate Cloud Engineer exam, I’d like to introduce this Google Cloud product as something that’ll be a significant security improvement to your infrastructure.
IAP allows you to securely connect to your instances without a public IP address to both Linux and Windows operating systems. IAP provides a single point of control for managing users and access to systems with just HTTPS access, as can be seen in the following diagram (for more details, refer to https://cloud.google.com/iap/images/iap-load-balancer.png):
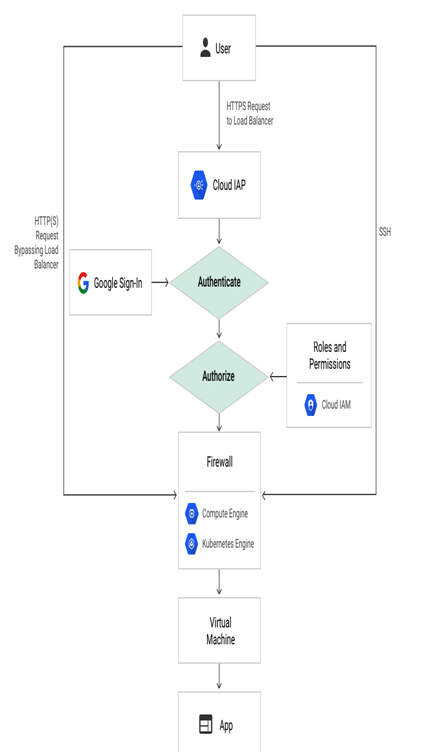
Figure 4.26 – Access to VMs with IAP
To learn more about IAP, visit the Google Cloud documentation: https://cloud.google.com/iap/docs/concepts-overview.
Linux instances
For our purposes, we will not use IAP or OS login, which is available to connect to Linux instances. Still, we encourage you to try to connect to both possibilities using both options.
Console
Instances can be accessed from within the Cloud console itself by using Cloud Shell or any other software of your preference available on your operating system.
The following screenshot shows the different ways to connect to a Linux instance:
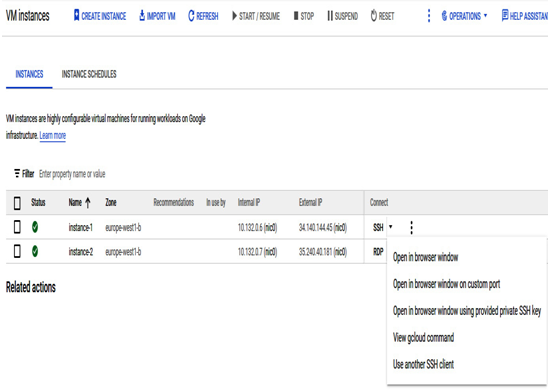
Figure 4.27 – A Linux instance with options to connect via SSH
We have many options on how we can connect to the instance. They are as follows:
- Open an SSH connection in the browser window
- Open an SSH connection in the browser window on a custom port
- Open SSH connection in the browser window using a provided private SSH key
The most straightforward connection can be achieved by clicking on the SSH button, and a new window will open where we have full access to the instance:
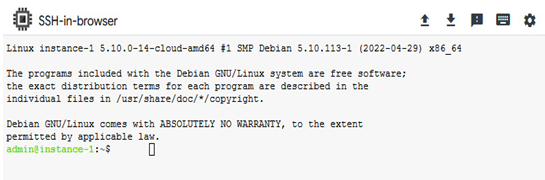
Figure 4.28 – In the browser, an SSH connection to the instance
This connectivity is effortless to establish and use.
Command line
To access an instance from the Cloud Shell, we need to execute the following command:
gcloud compute ssh –zone “zone_name” “instance_name” –project “project_name”
The following screenshot shows that the connection to Cloud Shell using the gcloud command is very easy to establish.
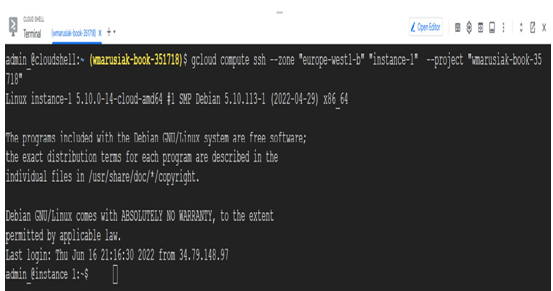
Figure 4.29 – An SSH connection to the instance from Cloud Shell
As many SSH clients are available for many operating systems, it is impossible to cover them all in this book.
The following screenshot shows the SSH session established with the instance, using its public IP address and the PuTTY SSH client from the Windows operating system:
Figure 4.30 – An SSH connection to the instance from Cloud Shell
Connecting to instances is quite an important topic, and we strongly advise trying out connectivity via the SSH protocol.
