Configure Azure Storage firewalls and virtual networks
Storage accounts are managed through Azure Resource Manager. Management operations are authenticated and authorized using Microsoft Entra ID RBAC. Each storage service exposes its own endpoint used to manage the data in that storage service (blobs in Blob Storage, entities in tables, and so on). These service-specific endpoints are not exposed through Azure Resource Manager; instead, they are (by default) internet-facing endpoints.
Access to these internet-facing storage endpoints must be secured, and Azure Storage provides several ways to do so. In this section, you will review the network-level access controls: the storage firewall and service endpoints. This section also discusses Blob Storage access levels. The following sections then describe the application-level controls: shared access signatures and access keys. In later sections, you will learn about Azure Storage replication and how to leverage Microsoft Entra ID authentication for a storage account.
Storage firewall
Using the storage firewall, you can limit access to specific IP addresses or an IP address range. It applies to all storage services endpoints (blobs, tables, queues, and files). For example, by limiting access to the IP address range of your company, access from other locations will be blocked. Service endpoints are used to restrict access to specific subnets within an Azure virtual network.
To configure the storage firewall using the Azure portal, open the storage account blade and click Networking. Under Public Network Access, select Enabled From Selected Virtual Networks And IP Addresses to reveal the Firewall and Virtual Networks settings, as shown in Figure 2-6.
When accessing the storage account via the internet, use the storage firewall to specify the internet-facing source IP addresses (for example, 32.54.231.0/24, as shown in Figure 2-6) which will make the storage requests. All internet traffic is denied, except the defined IP addresses
in the storage firewall. You can specify a list of either individual IPv4 addresses or IPv4 CIDR address ranges. (CIDR notation is explained in Skill 4.1 in Chapter 4, “Configure and manage virtual networking.”)
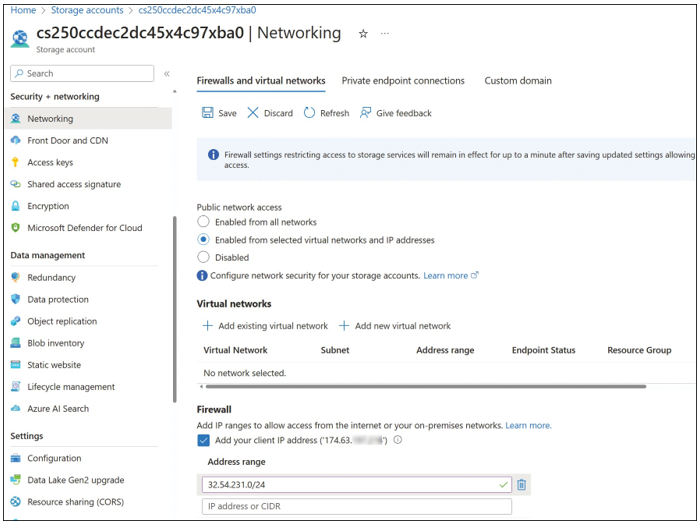
FIGURE 2-6 Configuring a storage account firewall and virtual network service endpoint access
The storage firewall includes an option to allow access from trusted Microsoft services. As an example, these services include Azure Backup, Azure Site Recovery, Azure Networking, and more. For example, it will allow access to storage for NSG flow logs if Allow Trusted Microsoft Services To Access This Account is selected. Separately, you can enable Allow Read Access To Storage Logging From Any Network or Allow Read Access To Storage Metrics From Any Net- work to allow read-only access to storage metrics and logs.

