Configure Microsoft Entra Join
Microsoft Entra includes the ability to manage device identity, which enables single sign-on to devices and the applications and services managed through Entra that are accessed from that device. Managed devices include both enterprise and bring-your-own-device (BYOD) scenarios. This allows users to work from any device, including personal devices, all while protecting corporate intellectual property with the necessary regulatory and compliance controls.
Using Entra ID Join, you can control these devices, the applications installed and accessed from them, and how those applications interact with your corporate data.
When associating devices with Entra, you have three options: Register A Device, Join A Device, and Use Hybrid Joined. Registering devices would be appropriate for personal devices, while joining devices is useful for corporate-owned devices. Hybrid joined devices are joined to your on-premises Active Directory and are registered with your Entra ID tenant.
When you associate a device with Entra ID, you can manage a device’s identity by imple- menting features like single sign-on (SSO) and securing access using conditional access. Note that this identity can be managed independently of a user’s identity. This provides a great degree of flexibility because devices can be enabled or disabled without affecting a user account. Entra ID Join is an extension of device registration that changes the local state of the device. When a device is Entra-joined, users can sign in to the device using an organizational account instead of a personal account.
Also, registration of devices in Entra can be combined with a mobile device management solution, such as Microsoft Intune, Microsoft Endpoint Configuration Manager, Mobile Appli- cation Management (MAM), and Group Policy if it is hybrid joined. This allows for additional device attributes—such as device operating system version and device state (including whether the device is rooted or jailbroken)—to be tracked in Entra ID. Those attributes can then be used to build and enforce conditional access policies, which can further secure corporate data.
To configure device registration in Entra ID, choose Devices, Device Settings. On the Device Settings blade, you can set the configuration for an entire Entra ID tenant, as seen in Figure 1-12.
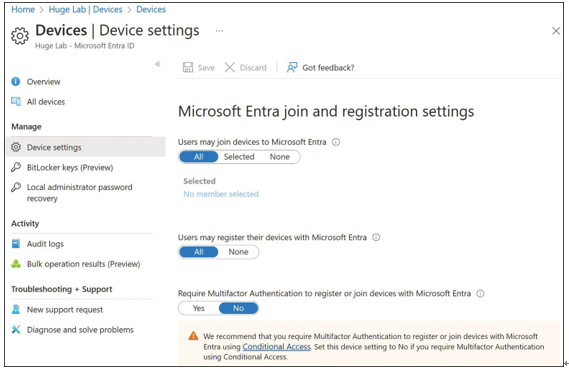
FIGURE 1-12 Configure device registration settings
On this blade, you can configure the following settings:
- Users May Join Devices To Microsoft Entra Use this setting to select the users and groups that can join devices to Entra. This setting only applies to Entra Join on Windows 10 or Windows 11 devices. The default value is All and can be changed to Selected or None.
- Additional Local Administrators On Microsoft Entra Joined Devices With Entra ID Premium or with the Enterprise Mobility + Security suite, you can choose which users are granted Local Administrator rights to the device. Global Administrators and the device owner are granted Local Administrator rights by default. The default value is None and can be changed to Selected. If the value is set to Selected, any users added here are also added to the Device Administrators role in Entra ID.
- Users May Register Their Devices with Microsoft Entra Allow users to register their devices with Microsoft Entra (Workplace Join). Enrollment with Microsoft Intune or Mobile Device Management for Office 365 requires device registration. If you have configured either of these services, All will be selected, and the button associated with the setting will be disabled.
- Require Multifactor Auth To Join Devices Multifactor authentication (MFA) is recommended when adding devices to Entra. When set to Yes, users who are adding devices from the internet must first use a second method of authentication. Prior to enabling this setting, you must ensure that multifactor authentication is configured for the users who are able to register devices and that those users have set up MFA.
- Maximum Number Of Devices Per User This setting designates the maximum number of devices that an individual user can have in Entra ID. If the quota is reached, the user will not be able to add a device until one of their existing devices is removed. Valid values for this setting are 5, 10, 20, 50, 100, and Unlimited.

After the directory has been configured, you can begin registering devices. For Entra Join, there are several requirements for devices, including Windows versions. The requirements for Windows versions are driven by the type of Entra Join: hybrid or non-hybrid. Non-hybrid Entra Join is applicable to devices that are not joined to an on-premises Active Directory, whereas hybrid Entra Join is applicable to devices that are joined to an on-premises directory. For hybrid Entra Join, an IT administrator must perform the join to Entra ID.
For non-hybrid Entra Join, Windows 10 and Windows 11 Professional as well as Windows 10 and Windows 11 Enterprise devices can be joined to a directory. For hybrid Entra Join scenarios, you can join current Windows devices, such as Windows 11 and Windows Server 2016. Also, there is support for a hybrid join with down-level devices, including Windows 7, Windows 8.1, Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, and Windows Server 2012 R2.
