Azure resource locks (sometimes called management locks) are used to prevent the accidental deletion or modification of resources. There are two types of locks:
- Delete locks prevent the deletion of a resource. A Delete lock only prevents deletion of a resource and does not impede the modification of a resource.
- Read-only locks prevent users from modifying a resource, which includes updating or deleting a resource.
Note that both types of resource locks allow authorized users to read resources; resource locks apply across all users and roles, even custom and privileged roles.
Resource locks, regardless of type, can be applied to the subscription, resource group, and resource scopes. When you apply a lock to a scope, the resources within that scope inherit the lock. This means that a lock applied to the resource group scope applies to all the resources in the resource group. Resource locks apply to all service instances and resources within a scope.
Lock inheritance applies to the child resources of the scope that you are configuring the lock on. For example, a lock on a resource group applies to all resources in the group. If a Delete lock is applied to one of the resources in the resource group and you attempt to delete that resource group, it will fail. When you try to delete the resource group, the operation tries to delete all the underlying resources first and won’t be able to delete the resource with a Delete lock, hence the resource group deletion would also fail.
Note that resource locks get applied to the management plane of Azure. This means resource locks don’t affect the resource’s own functionality; instead, they restrict the interac- tions with other Azure resources. For example, a Read-only lock applied to a storage account would prevent users from reading the access keys. If you attempt to read or modify the access keys, the operation will fail with a “Cannot perform write operation because the following scope(s) are locked” error, as shown in Figure 1-39.
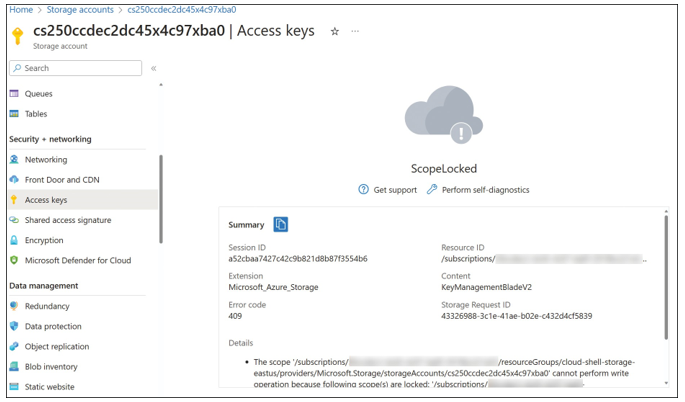
FIGURE 1-39 Read-only lock applied to a storage account
When creating locks, exercise caution because they can cause unexpected results. Many operations appearing to be read operations require write access within the Azure management plane. For example, the same Read-only lock on a storage account would prevent users from creating new blob containers because the action requires write access.
Once you have determined the type of lock you will apply based on your requirements, you can apply the lock through the Azure portal, Azure PowerShell, the Azure CLI, Resource Manager templates, or the REST API.
To create a lock through the Azure portal, browse to the desired scope and select the Locks blade. From the blade, click Add to create a new lock. Give the lock a Lock Name, select the Lock Type, and describe the lock in the Notes field, as shown in Figure 1-40.
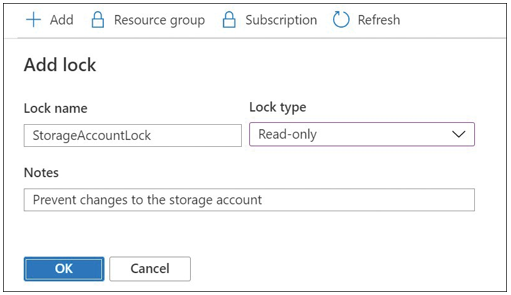
FIGURE 1-40 Creating a lock
