Configure storage account encryption
Data in an Azure storage account is encrypted using AES 256-bit encryption and is FIPS 140-2 compliant. Encryption in an Azure storage account is enabled automatically and cannot be disabled.
By default, Microsoft manages the keys used to encrypt and decrypt the data. In this sce- nario, Microsoft is responsible for key storage, rotation, control, and scope. If your organization has business or compliance requirements to manage these components, the Azure storage account can be configured to use customer-managed keys. This key would be used to encrypt the data for blob and file storage only.
Using customer-managed keys requires two additional Azure components: Azure Key Vault and a managed identity. The Azure Key Vault acts as the secure repository to store the key that you select for encryption operations in the storage account. The managed identity is used by the storage account to access and retrieve the key from the key vault.
To configure encryption for an Azure storage account, select Encryption from the Storage Account menu. On the Encryption tab, select Customer-managed Keys. This will show the addi- tional configuration items, where you can select an existing key vault, identity type, and key.
Figure 2-27 displays the Encryption page.
Manage data using Azure Storage Explorer
Azure Storage Explorer is a cross-platform application designed to help you quickly manage one or more Azure storage accounts. It can be used with all storage services: Blob Storage, Azure Tables, Queue Storage, and Azure Files. In addition, Azure Storage Explorer also sup- ports the CosmosDB and Azure Data Lake Storage services.
You can install Azure Storage Explorer by navigating to its landing page at https://azure. microsoft.com/features/storage-explorer/ and selecting your operating system (Windows, macOS, or Linux).
In addition, a browser-based storage explorer with similar functionality is integrated into the Azure portal. To access it, click Storage Browser from the Storage Account blade.
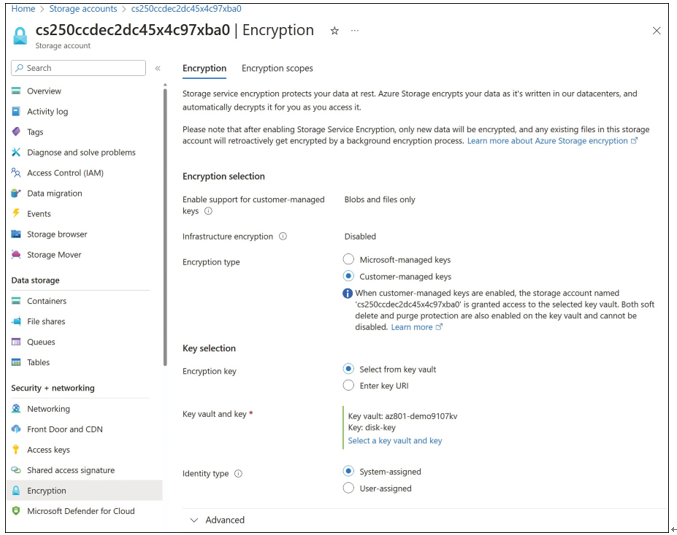
FIGURE 2-27 Storage account encryption
Connect Storage Explorer to Storage Accounts
After Storage Explorer is installed, you can connect to Azure Storage in a number of different ways (shown in Figure 2-28):
- Subscription This option allows you to sign in using a work or Microsoft account and access all your storage accounts via role-based access control.
- Storage Account or service This option requires you to have access to the storage account name and key. These values can also be accessed from the Azure portal under Access Keys.
- Blob container or directory Attach directly to only the blob service endpoint to interact with a container or directory.
- ADLS Gen2 container or directory Attach directly to only an Azure Data Lake Storage Gen2 container in a storage account.
- File share Attach directly to an Azure Files share that has already been created in a storage account.
- Queue Attach directly to the queue service endpoint of an existing storage account.
- Table Attach directly to the table service endpoint of an existing storage account.
- Local Storage Emulator Allows you to connect to the local Azure Storage emulator as part of the Microsoft Azure SDK.
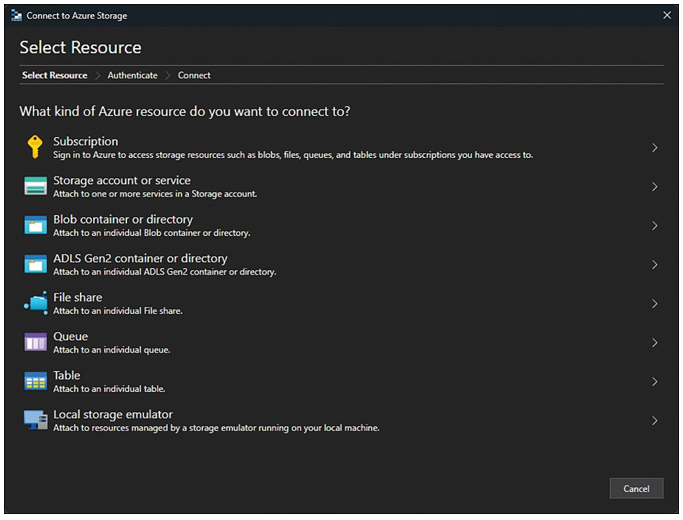
FIGURE 2-28 Connecting to an Azure storage account using Azure Storage Explorer
After connecting, filter which subscriptions to use. Once you select a subscription, all the supported services within the subscription will be made available. Figure 2-29 shows an expanded Azure Storage container named examref.
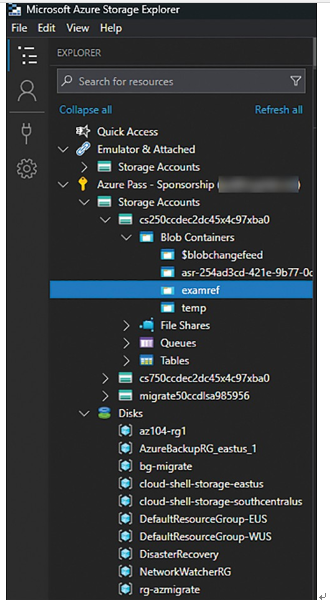
FIGURE 2-29 Azure Storage Explorer showing an Azure storage account beneath the subscription
