VPN is often considered the fastest way to connect to Google Cloud. It uses a public network and doesn’t require additional physical connection setup. Two types of Cloud VPN gateways at Google Cloud are high availability (HA) VPN and Classic VPN. Classic VPN doesn’t offer high availability and BGP support. It only supports static routing. Google recommends using HA VPN whenever possible and Classic VPN only in cases where on-premises VPN devices don’t support BGP. This section will focus on the HA VPN type of gateway.
A VPN gateway is a regional resource that uses IPSec tunnels with IKE encryption to establish a secure connection over the internet. It uses a pre-shared key to encrypt the traffic, so both sides of the connection need to know the key. Cloud VPN comes with external IP addresses that will be used to create tunnels over a public network. Although it is possible to set up only one tunnel, two or four (to another cloud provider) are required for 99.99% availability. Each Cloud VPN tunnel supports up to 3 Gbps together for ingress and egress traffic.
The following screenshot presents an example of a VPN tunnel configuration between the Google Cloud VPC global-vpc and on-premises devices. Although VPC is global and has subnets in the europe-cental2 (10.0.1.0/24), australia-southeast (10.0.2.0/24), and us-west4 (10.0.3.0/24) regions, VPN Gateway and Cloud Router are regional resources, which in this case are deployed in the europe-central2 region only. The VPN gateway has two interfaces, each with a Public IP, that are used to set up two tunnels to the on-premises site. On the on-premises site, there are two VPN gateways, each with one interface with a public IP address. Behind the VPN gateways is a router that has a route to an on-premises subnet (10.99.0.0/24). Both sides are connected with two VPN tunnels. Two BGP sessions are established between Cloud Router (ASN 64512) and the on-premises router (ASN 64513). Assuming Cloud Router uses default route advertisement and the VPC uses global routing, routes to all VPC subnets are advertised by Cloud Router and visible to the on-premises router. Also, the on-premises route, 10.99.99.0/24, is visible to all subnets in global-vpc. Note that even if routes are visible, end-to-end communication between workloads in the cloud and on-premises is still controlled by firewalls that need to allow this external traffic:
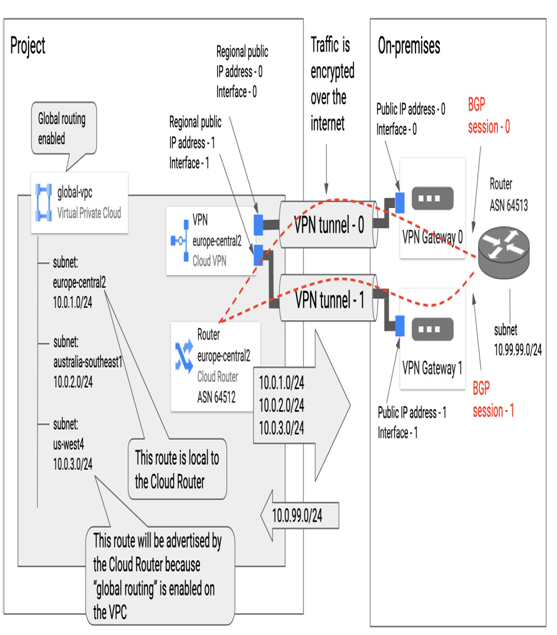
Figure 9.18 – Example of a VPN setup between a Google Cloud VPC and an on-premises environment
The following steps are required on the Google Cloud side to set up a VPN between Google Cloud and on-premises or another cloud:
- Create a Cloud Router in a selected region, as presented in Figure 9.17.
- Create a Cloud VPN gateway for the same region and VPC where the Cloud Router was configured. When a gateway is created, public IP addresses of its interfaces are generated and published so that they can be used to configure the tunnels on the other side.
- Add a peer VPN gateway (on-premises/other cloud side) by providing a name and number of VPN interfaces, along with their public IP addresses.
- It is also possible to create a VPN connection between two VPCs in the same or a different Google Cloud project. In this case, you need to have access to peer resources. Also, a Cloud VPN gateway and a Cloud Router in this project need to exist before this setup.
- Add VPN tunnels between both ends. Each tunnel needs to have a unique name. In this step, you must also set up IKE encryption and generate a pre-shared key.
- Configure peer tunnel endpoints on the on-premises/another cloud side.
- Configure a BGP session for each tunnel, where you provide the name and ASN of a peer router. You can decide to set up BGP IP and peer BGP IP addresses manually or automatically. During the BGP session setup, you can choose to either advertise all routes visible to the Cloud Router or create custom routes.
- The same BGP session setup needs to be created on the on-premises/other cloud side. It is recommended that you aggregate routes on-premises and ensure they don’t overlap with the VPC subnet ranges.
Now that we’ve covered the steps to establish a VPN connection between on-premises and Google Cloud networks in a VPC, we can consider another option: creating Cloud Interconnect. We will also examine the differences between these two approaches
