Identity and Access Management
When it comes to accessing your AWS account and working inside it, you need the Identity and Access Management (IAM) services of AWS. IAM allows you to grant access to other individuals for team management of the services. IAM permits extremely granular permissions. For example, you might grant someone read access to only a single bucket of objects in S3. Other features of IAM include the following:
Access from service to service in AWS: For example, you can have an application running on an EC2 instance access an S3 bucket. As you will learn later in this chapter, roles are commonly used for such access.
Multifactor Authentication (MFA): Access can be permitted using a password and a code from an approved device to greatly strengthen security. Figure 9-1 shows the configuration area for MFA in the IAM Management Console.
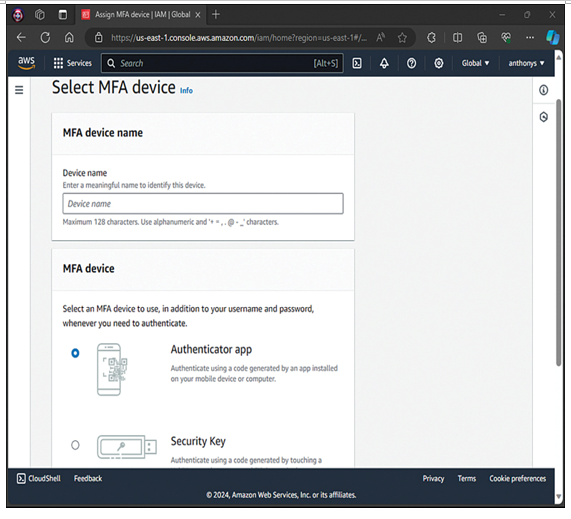
Figure 9-1 Configuring MFA for an Account
Identity federation: With federation, users who have already authenticated with another service can gain temporary access to resources and services in your account.
Identity information for assurance: CloudTrail can trace and log all SPI activity against every service and resource in your account. Figure 9-2 shows the CloudTrail Dashboard in AWS.
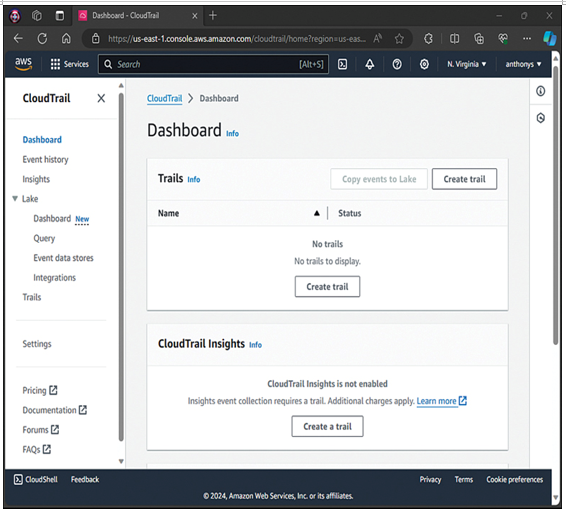
Figure 9-2 The CloudTrail Dashboard
PCI DSS compliance: IAM supports the processing, storage, and transmission of credit card data by a merchant or service provider, and it has been validated as being compliant with the Payment Card Industry (PCI) Data Security Standard (DSS).
Integration: In order to be successful, IAM integrates with every major service of AWS, including EC2, EFS, VPC, and RDS.
Always free: While some services of AWS can be free for one year (using the Free Tier account), IAM services remain free for the life of your account.
Accessibility options: You can access the components of IAM in a variety of ways, including using the AWS Management Console, AWS command-line tools, AWS SDKs, and the IAM HTTPS API.
It is critical that you understand the main identities you’ll use in IAM. Please realize that there is much more to IAM than these identities, but at this point in your AWS education, you need to know the main foundational components.
Identities consist of the following:
AWS account root user: This is the account you established when you signed up for AWS, and the username for this account is the email address used for signup. We discuss this account in greater detail later in the chapter.
Users: A user is an entity that you create in AWS to represent a person or service that interacts with AWS. When you create an IAM user, you grant it permissions by making it a member of a group that has appropriate permissions policies attached (which is the recommended method) or by directly attaching policies to the user. You can also clone the permissions of an existing IAM user, which automatically makes the new user a member of the same groups and attaches all the same policies. Figure 9-3 shows a user in AWS.
Groups: A group is a collection of IAM users. You can use a group to specify permissions for a collection of users, which can make those permissions easier to manage for those users.
Roles: A role is similar to a user account, but it does not have any credentials (password or access keys) associated with it. One powerful use of roles in AWS is to use them to enable one service to securely access another service within AWS.

Figure 9-3 A User in AWS IAM
