IaC is a new way to deploy and manage infrastructure. It doesn’t only apply to cloud resources but to on-premises resources – for example, VMware vSphere. However, this book and this chapter will focus on IaC deployment in Google Cloud.
We briefly mentioned IaC in Chapter 2, where we discussed various ways of deploying resources in Google Cloud – Cloud Foundation Toolkit, Config Connector, and Terraform.
IaC aims to solve main issues from the past – lengthy time to deliver resources, errors during the deployment, ease of implementation, and the overall complexity of IT resource management.
Config Connector in Google Kubernetes Engine
In Chapter 5 and 6 we learned how to create, configure, and use Google Kubernetes Engine (GKE) to deploy applications. We will use that knowledge to install, configure, and deploy Config Connector and Google Cloud resources. Config Connector is an open source Kubernetes add-on that allows us to manage Google Cloud resources in a Kubernetes way.
To use Config Connector, there are a few prerequisites that GKE needs to have:
- GKE version:
- 1.15.11-gke.5 and later
- 1.16.8-gke.8 and later
- 1.17.4-gke.5 and later
- A Workload Identity Pool needs to be enabled
- GKE monitoring must be enabled
We will start by installing Config Connector on the newly created GKE cluster.
Installing Config Connector
As mentioned previously, Config Connector is an add-on to GKE. We can enable it during GKE cluster creation or reconfigure the existing GKE cluster to support it.
New GKE cluster
As mentioned previously, we must ensure that all the prerequisites have been met:
- Go to GKE in Cloud Console.
- Click Create and choose GKE Standard.
- Provide the name of your GKE cluster.
- Choose the supported GKE master version.
- In the Security part of the cluster, select Enable Workload Identity:
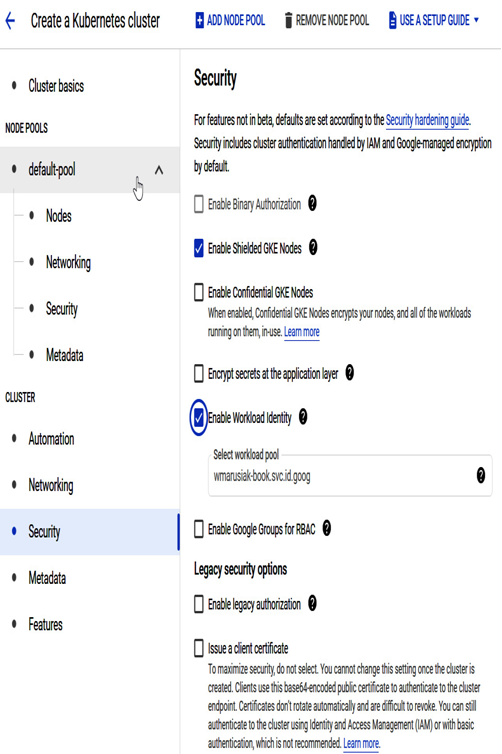
Figure 7.27 – Workload Identity configuration in the Security section of the newly created GKE cluster
6. In the Features section of the cluster, click Enable Config Connector:
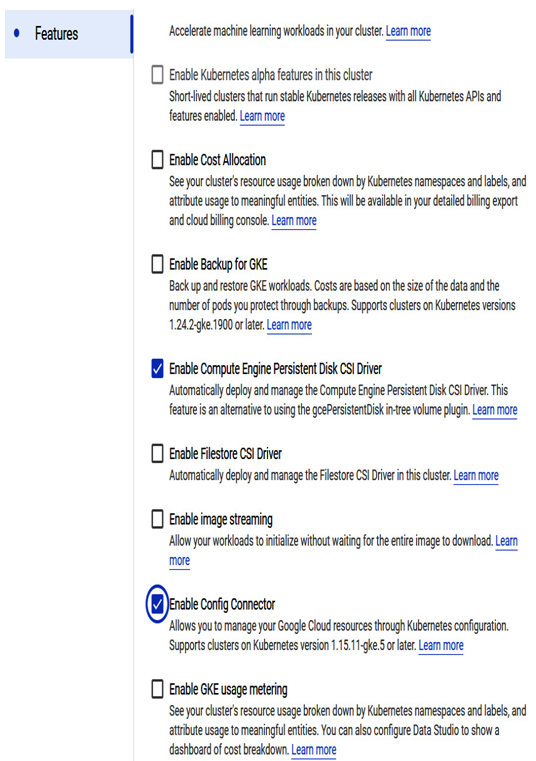
Figure 7.28 – Config Connector configuration in the Security section of the newly created GKE cluster
7. Monitoring must also be enabled and selected by default with newly created GKE clusters.
8. Now that we’ve created the cluster, Config Connector is ready to be used.
Next, we will enable Config Connector in the existing GKE cluster.
