To manage access (role) assignments, you can use the Azure portal, the Azure CLI, Azure PowerShell, Azure SDKs, or the Resource Manager REST APIs. The following section describes how to manage role assignments using the Azure portal.
In the Azure portal, the Access Control (IAM) blade is used to manage access to resources, and it is where role assignments are applied or removed. The Access Control (IAM) blade is available at any scope where role assignments can be made (management group, subscription, resource group, and resource). To find the Access Control (IAM) blade, navigate to the resource or service where you want to manage role assignments.
In the following example, the Virtual Machine Contributor built-in role will be assigned to a user at the resource group scope.
In the Azure portal, navigate to a resource group by selecting Resource Groups on the left, selecting a resource group, and then selecting the Access Control (IAM) blade.
From the Access Control (IAM) blade, you can
- Check the effective access rights for a security principal at the current scope through the Check Access tab, where you can also view access rights inherited from a parent scope
- Edit role assignments, both granting and revoking access rights through the Role Assignments tab
- View deny assignments, which are controlled by Microsoft, through the Deny Assignments tab
- View and manage permissions to classic resources through the Classic Administrators tab
- View the available roles, both built-in and custom, through the Roles tab
To create a role assignment, navigate to the Role Assignments tab and click Add, as shown in Figure 1-25.
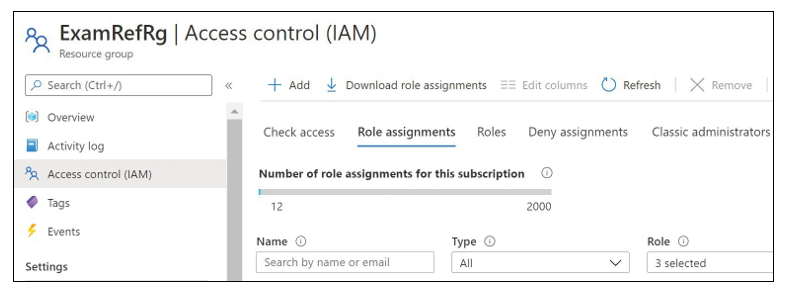
FIGURE 1-25 Role Assignments tab on the Access Control (IAM) blade
After clicking Add, select Add Role Assignment, as shown in Figure 1-26.
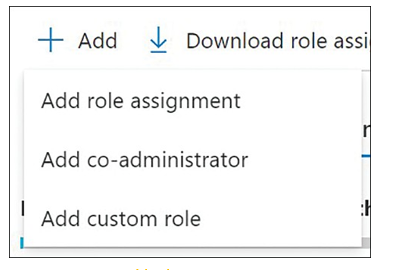
FIGURE 1-26 Add role assignment
On the Add Role Assignment blade, there are three tabs: Role, Members, and Review + Assign. The Role tab lists roles as job function roles or privileged administrator roles. Select the role from the Role tab that you plan to assign, then on the Members tab, select the user, group, security principal, or managed identity you want to assign the role to. Click Review +
Assign when you are done. Figure 1-27 shows an example where the user, DemoUser@hugelab. net, is being granted access to the Virtual Machine Contributor role. In the example directory, two security principals were returned from the filtered list using the search term “User”—(VM User and Demo User). A single principal (Demo User) was selected (displayed under Selected Members) to apply to the Virtual Machine Contributor role assignment.
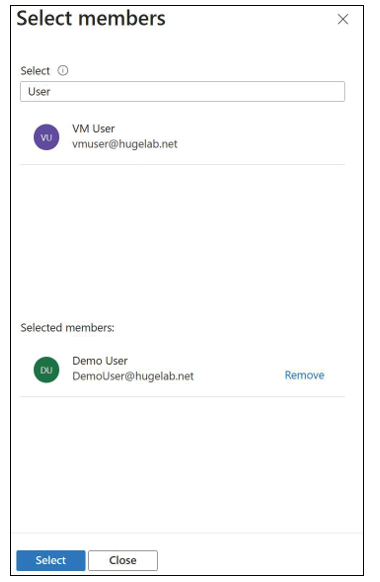
FIGURE 1-27 Select members
After clicking Review + Assign, you will see the role assignment on the Role Assignments tab. To remove a role assignment, select one or more security principals and click Remove. An example is shown in Figure 1-28.
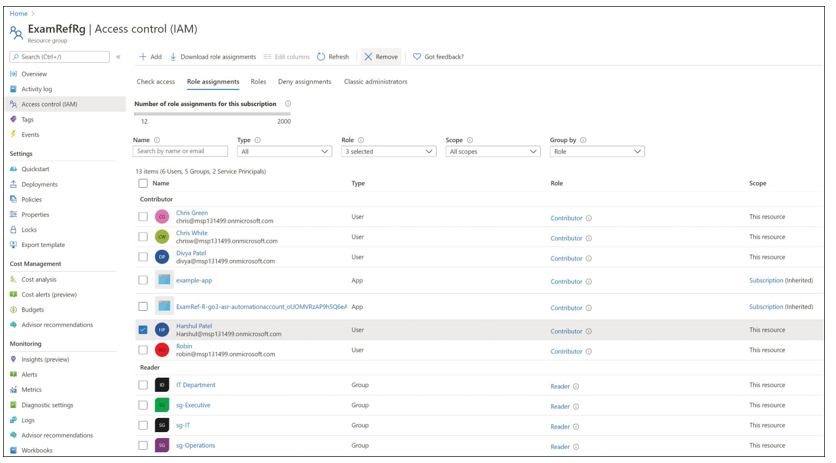
FIGURE 1-28 Remove a role assignment
