Man-in-the-Middle Attack (39.6.5)
In a man-in-the-middle (MITM) attack, also known as an on-path attack, the hacker is positioned in between two legitimate entities in order to read or modify the data that passes between the two parties. There are many ways in which to create an MITM attack.
A popular wireless MITM attack is called the “evil twin AP” attack, where an attacker introduces a rogue AP and configures it with the same SSID as a legitimate AP, as shown in Figure 39-23. Locations offering free Wi-Fi, such as airports, cafes, and restaurants, are particularly popular spots for this type of attack due to the open authentication.
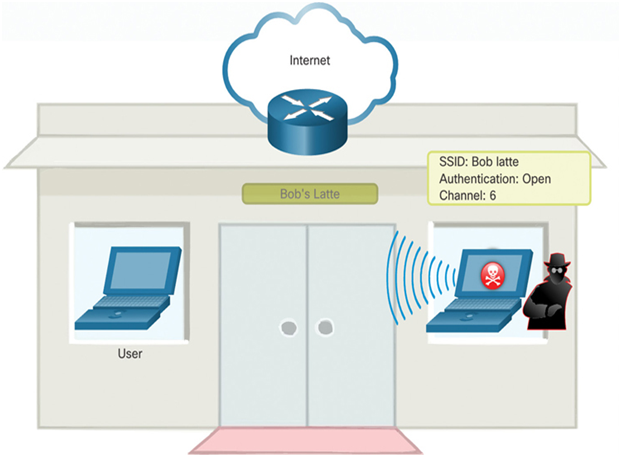
Figure 39-23 Example of an MITM Attack
MITM attacks and their variations are frequently referred to as on-path attacks.
Wireless clients attempting to connect to a WLAN would see two APs with the same SSID offering wireless access. Those near the rogue AP find the stronger signal and most likely associate with it. User traffic is now sent to the rogue AP, which in turn captures the data and forwards it to the legitimate AP, as shown in Figure 39-24. Return traffic from the legitimate AP is sent to the rogue AP, captured, and then forwarded to the unsuspecting user. The attacker can steal the user’s passwords and personal information, gain access to their device, and compromise the system.
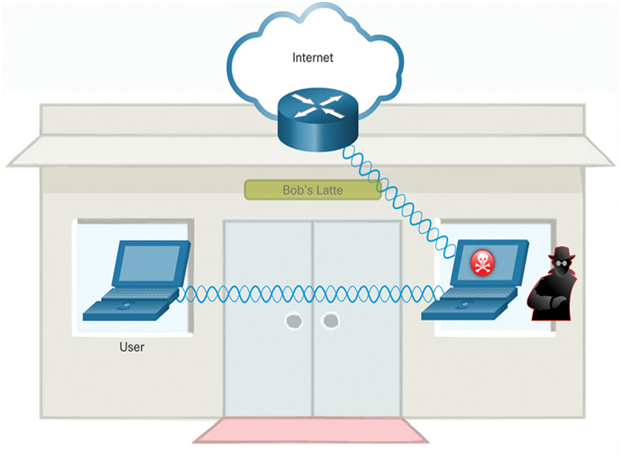
Figure 39-24 Example of a Rogue AP
Defeating an attack like an MITM attack depends on the sophistication of the WLAN infrastructure and the vigilance in monitoring activity on the network. The process begins with identifying legitimate devices on the WLAN. To do this, users must be authenticated. After all of the legitimate devices are known, the network can be monitored for abnormal devices or traffic.
Check Your Understanding—WLAN Threats (39.6.6)
Refer to the online course to complete this activity.
Video—Secure WLANs (39.6.7)
The previous topic explained the WLAN threats. What can you do to secure the WLAN?
Refer to the online course to view this video.
SSID Cloaking and MAC Address Filtering (39.6.8)
Wireless signals can travel through solid matter, such as ceilings, floors, walls, outside of the home, or office space. Without stringent security measures in place, installing a WLAN can be the equivalent of putting Ethernet ports everywhere, even outside.
To address the threats of keeping wireless intruders out and protecting data, two early security features were used and are still available on most routers and APs: SSID cloaking and MAC address filtering.
APs and some wireless routers allow the SSID beacon frame to be disabled, as shown in Figure 39-25. Wireless clients must manually configure the SSID to connect to the network.
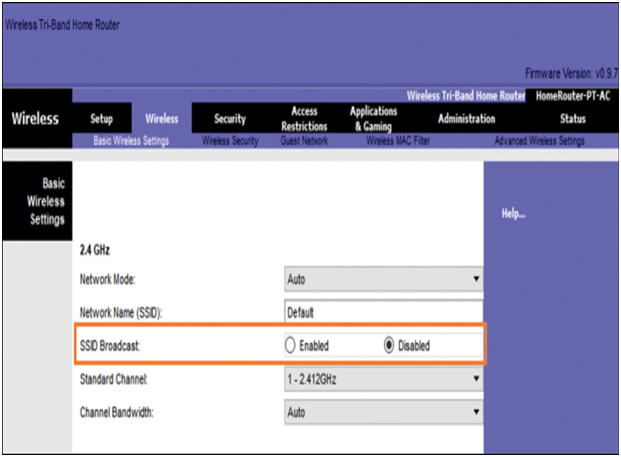
Figure 39-25 Example of Disabled SSID Broadcast
An administrator can manually permit or deny clients wireless access based on their physical MAC hardware address. In Figure 39-26, the router is configured to permit two MAC addresses. Devices with different MAC addresses will not be able to join the 2.4 GHz WLAN.
Figure 39-26 Example of Filtering MAC Addresses
