Controlling resource groups with Azure Policy is done by scoping the assignment of policy and initiatives. Recall that Azure Policy supports multiple scopes:
- Management group Assignments scoped at the management group (either the Ten- ant Root Group or a child group) apply to all child resources in the management group including child management groups, all subscriptions, resource groups, and resources.
- Subscription Assignments scoped to a subscription apply to all child resources in the subscription resource groups and resources.
- Resource group Assignments scoped to a resource group apply to all child resources in the resource group.
When creating assignments, it is also possible to configure excluded scopes. You can always
exclude a subscope. For example, when scoping an assignment to a management group, any subscriptions, resource groups, or even resources that are children of the management
group, can be excluded. When scoping an assignment to a subscription, child resource groups and resources can be excluded. When scoping an assignment to a resource group, only child resources can be excluded.
The flexibility of policy scoping is a powerful feature of Azure Policy. This allows you to model your environments with rich declarations in the form of policy definitions that are applied exactly as required by your organization’s governance needs.
Imagine you have an environment with the following requirements:
- All resources should be tagged with the tag “Environment” and the value “Dev/Test”.
- Only A-Series and D-Series virtual machines can be created, specifically Standard A0, A1,and D2 virtual machines that are not promotional.
- Resources in the rgCoreNetwork resource group are exempt from these policies.
To model this environment with Azure Policy, you can create two policy definitions (or use built-in policy definitions where applicable), as shown in Table 1-2.
TABLE 1-2 Azure Policy definitions example
| Policy Field | Policy Effect | Description |
| Type | Deny | Do not create virtual machines if they are not in the A-Series or D-Series SKU. |
| tags | Append | Append tag name “Environment” and tag value “Dev/Test” to all resources. |
- In the Azure portal, browse to the Policy service and select the Definitions blade.
To reduce administrative overhead, a new initiative definition will be created. Initiative definitions are a collection of policy definitions that are focused on the same goal. They allow for a set of policies to be grouped as a single item.
2. From the Definitions blade, click Initiative Definition, as shown in Figure 1-33.
FIGURE 1-33 Azure Policy Definitions blade
- Type Dev/Test Compliance into the Name field, select the Definition Location, and choose Create New from the Category options. Type Custom in the Category field, as shown in Figure 1-34.
- On the Policies tab, select Add Policy Definition(s) to add built-in policy definitions to the initiative. In this example, add the following built-in policies to the definition and set the values as noted (see Figure 1-35):
■ Require A Tag And Its Value On Resources
■ Allowed Virtual Machine Size SKUs
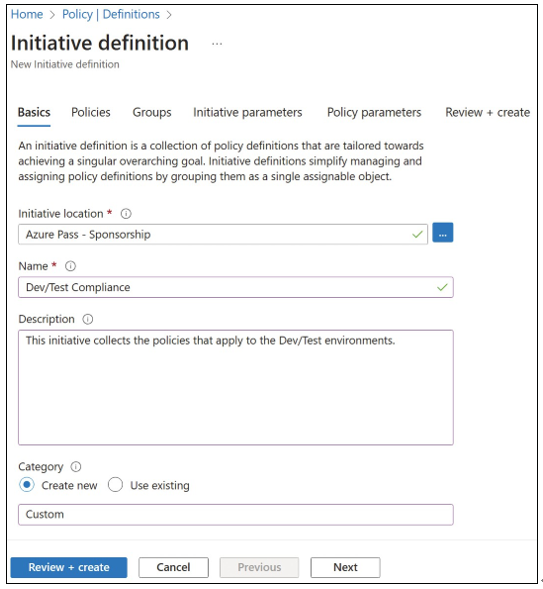
FIGURE 1-34 Azure Policy Initiative Definition blade
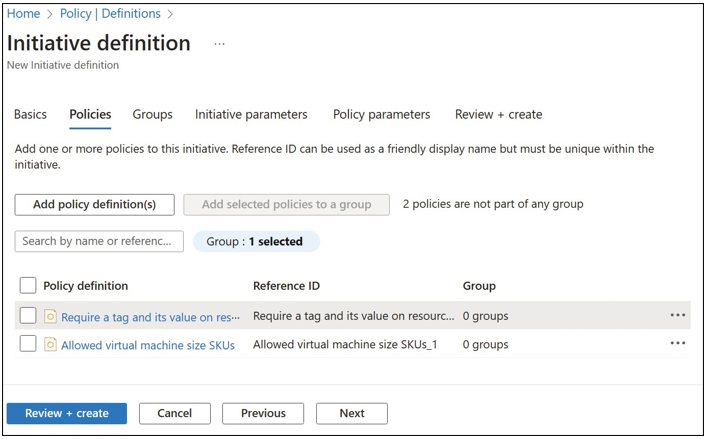
FIGURE 1-35 New initiative definition policies and parameters for Azure Policy
- Select the Policy Parameters tab. You will be prompted to provide default values for the policy definitions that were added to the initiative. In this scenario, add the following tag name and value:
■ Name: Environment
■ Value: Dev/Test - In the Allowed Size SKUs drop-down menu, select three sizes available for your subscription.
- Click Review + Create to save the definition so it can be used in an initiative assignment.
From the Policy page, browse to the Assignments blade and click Assign Initiative (see Figure 1-36).
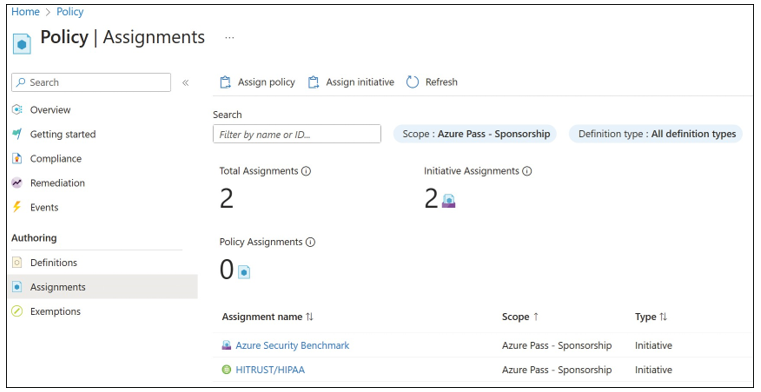
FIGURE 1-36 Azure Policy Assignments blade
8. To meet the environmental requirements, set the Scope of the assignment to the target subscription and configure the Exclusions to exclude the rgCoreNetwork resource group. Also, set the Initiative Definition to Dev/Test Compliance and set the Assignment Name to Dev/Test Compliance. Lastly, make sure Policy Enforcement is enabled (see Figure 1-37). Then click Review + Create, and click Create.
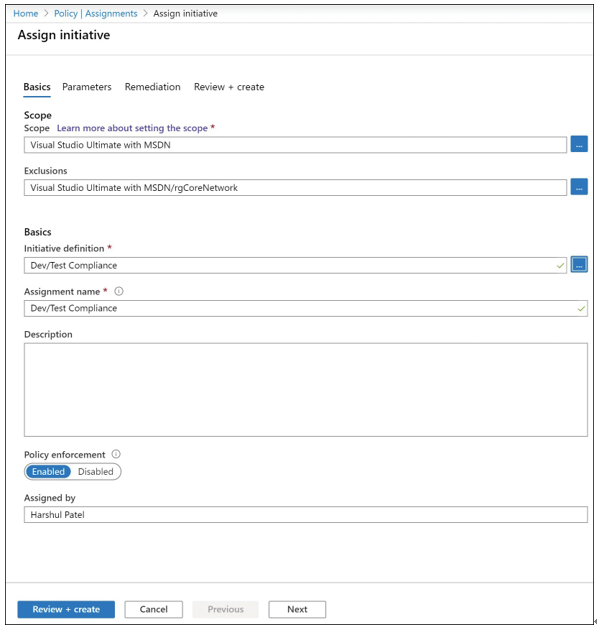
FIGURE 1-37 Azure Policy Assign Initiative blade
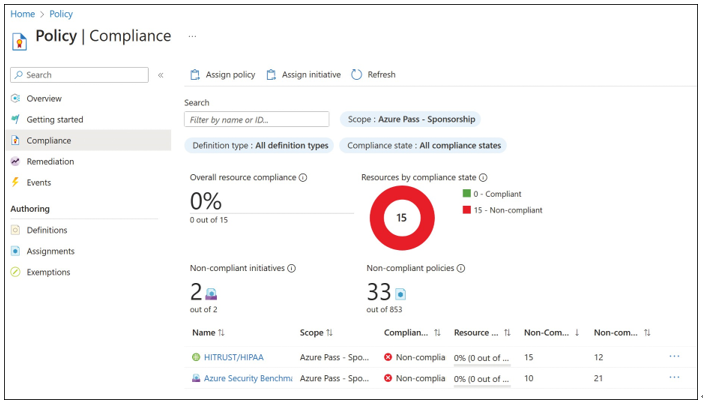
After policy definitions have been assigned, either through policy assignments or initia- tive assignments, the effects of the policy will be immediately applicable. Policy evaluation for compliance happens about once an hour, which means you might not be able to view the compliance state of a new assignment immediately.
Compliance state can be viewed on the Compliance blade of the Azure Policy service. You can delete, edit, and duplicate the policy assignment by right-clicking it on the Compliance blade, as shown in Figure 1-38.