Network Management Systems (37.6.5)
Network management refers to two related concepts. First is the process of configuring, monitoring, and managing the performance of a network. Second is the platform that IT and network operations teams use to complete these tasks. Modern network management platforms provide advanced analytics, machine learning, and intelligent automation to continually optimize network performance. As organizations adapt to a more distributed workforce, these network management systems are increasingly deployed in cloud and hosted environments.
Network management systems collect data from connected network devices such as switches, routers, access points, and client devices. They also give network administrators control over how those devices operate and interact with one another. The data captured from these devices is used to proactively identify performance issues, monitor security and segmentation, and accelerate troubleshooting.
Network management systems typically use Simple Network Management Protocol (SNMP) and Remote Network Monitoring (RMON) to gather information from network devices. Host operating systems have management platforms that allow monitoring and configuration of many host computers.
Network management systems are deployed using two operational models, as shown in Table 37-7.
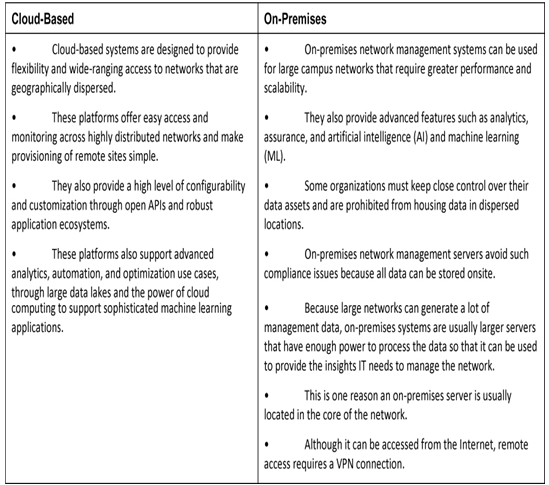
Table 37-7 Cloud-Based and On-Premises Comparison
Cisco Meraki is a leading cloud-based network management platform that provides powerful network management capabilities without consuming user bandwidth. It is secure, flexible, and easy to deploy. With it, networks can be managed from anywhere. It can manage a diverse range of both Meraki and non-Meraki network devices securely. It provides detailed views of large, dispersed, and complex networks down to the individual desktop computer or phone. Figure 37-45 provides a look at one aspect of a Meraki dashboard.
Figure 37-45 Meraki Dashboard
Video—What is Network Management? (37.6.6)
This video briefly explores network management including cloud network management and Cisco Nexus Dashboard.
Refer to the online course to view this video.
Network Support Summary (37.7)
The following is a summary of each topic in the chapter and some questions for your reflection.
What Did I Learn in This Chapter? (37.7.1)
• Diagnostics and Trouble Shooting Methodologies—Troubleshooting is a process that should be applied systematically. One approach uses a seven-step process in which the technician defines the problem, gathers relevant information, analyzes the information, eliminates possible causes, proposes a hypothesis about the most likely cause of the problem, and then tests the hypothesis and solves the problem. Another approach is to follow the layers of the OSI model.
Structured troubleshooting can include the use of seven different methods: bottom-up, top-down, divide-and-conquer, follow-the-path, substitution, comparison, and the educated guess approach.
The choice of method sometimes depends on the type of issue that is being addressed and the experience of the technician. It is important to always document the issue according to company procedures, including providing information of the eventual resolution of the problem.
• Network Documentation—Network documentation is essential to maintaining, securing, and troubleshooting networks. Documentation may consist of physical and logical network diagrams, written documents, and network performance baselines.
There are nine network topologies that may be documented. These includes personal area networks (PANs), local area networks (LANs), virtual LANs (VLANs), wireless LANs (WLANs), wireless mesh networks (WMNs), campus area networks (CANs), metropolitan area networks (MANs), wide area networks (WANs), and virtual private networks (VPNs).
Physical topology diagrams include the physical locations of devices and documents their connections. Logical topology diagrams include IP addresses and networking device details such as connected ports. Other information such as cloud services, routing policies, and security and remote-access policies may appear on topology diagrams.
Cloud services can be Software as a Service (SaaS), Platform as a Service (PaaS), or Infrastructure as a Service (IaaS). XaaS means anything/everything as a service, including desktop as a service (DaaS), disaster recovery as a service (DRaaS), communications as a service (CaaS), and monitoring as a service (MaaS).
Wireless standards define the operating characteristics of wireless operations, including signaling specifications, data rates, and power efficiency. Wireless standards form the IEEE 802.11 wireless Ethernet family of standards, such as 802.11b, n, g, and ac. These standards exist in the unlicensed wireless spectrum. Licensed wireless frequencies are controlled by the Federal Communications Commission (FCC) and licenses are granted to radio stations, cellular companies, and television stations.
Device documentation differs depending on the type of devices. It will often include device operating system and software, licensing information, interface status, addressing, routing protocols, etc.
