Packet Filtering Firewall Benefits and Limitations (39.5.4)
Packet filtering firewalls are usually part of a router firewall, which permits or denies traffic based on Layer 3 and Layer 4 information, as shown in Figure 39-16. They are stateless firewalls that use a simple policy table lookup that filters traffic based on specific criteria, as shown in the figure. For example, SMTP servers listen to port 25 by default. An administrator can configure the packet filtering firewall to block port 25 from a specific workstation to prevent it from broadcasting an email virus.
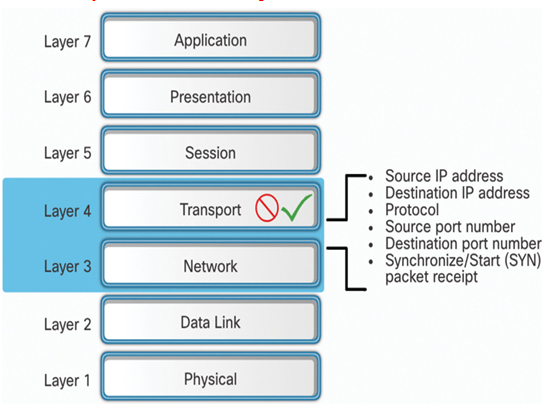
Figure 39-16 Packet Filtering at Layers 3 and 4
There are several advantages of using a packet filtering firewall:
- Packet filters implement simple permit or deny rule sets.
- Packet filters have a low impact on network performance.
- Packet filters are easy to implement, and are supported by most routers.
- Packet filters provide an initial degree of security at the network layer.
- Packet filters perform almost all the tasks of a high-end firewall at a much lower cost.
Packet filters do not represent a complete firewall solution, but they are an important element of a firewall security policy. There are several disadvantages of using a packet filtering firewall:
- Packet filters are susceptible to IP spoofing. Threat actors can send arbitrary packets that meet ACL criteria and pass through the filter.
- Packet filters do not reliably filter fragmented packets. Because fragmented IP packets carry the TCP header in the first fragment and packet filters filter on TCP header information, all fragments after the first fragment are passed unconditionally. Decisions to use packet filters assume that the filter of the first fragment accurately enforces the policy.
- Packet filters use complex ACLs, which can be difficult to implement and maintain.
- Packet filters cannot dynamically filter certain services. For example, sessions that use dynamic port negotiations are difficult to filter without opening access to a whole range of ports.
Packet filters are stateless. They examine each packet individually rather than in the context of the state of a connection.
Stateful Firewall Benefits and Limitations (39.5.5)
There are several benefits to using a stateful firewall in a network:
- Stateful firewalls are often used as a primary means of defense by filtering unwanted, unnecessary, or undesirable traffic.
- Stateful firewalls strengthen packet filtering by providing more stringent control over security.
- Stateful firewalls improve performance over packet filters or proxy servers.
- Stateful firewalls defend against spoofing and DoS attacks by determining whether packets belong to an existing connection or are from an unauthorized source.
- Stateful firewalls provide more log information than a packet filtering firewall.
Stateful firewalls also present some limitations:
- Stateful firewalls cannot prevent application layer attacks because they do not examine the actual contents of the HTTP connection.
- Not all protocols are stateful. For example, UDP and ICMP do not generate connection information for a state table, and, therefore, do not garner as much support for filtering.
- It is difficult to track connections that use dynamic port negotiation. Some applications open multiple connections. This requires a whole new range of ports that must be opened to allow this second connection.
- Stateful firewalls do not support user authentication.
Table 39-5 summaries the benefits and limitations of using stateful firewalls.

Table 39-5 Benefits and Limitations of Stateful Firewalls
