Packet Tracer—Use CDP to Map a Network (37.2.12)
A senior network administrator requires you to map the Remote Branch Office network and discover the name of a recently installed switch that still needs an IPv4 address to be configured. Your task is to create a map of the branch office network. To map the network, you will use SSH for remote access and the Cisco Discovery Protocol (CDP) to discover information about neighboring network devices, like routers and switches.
Refer to the online course to complete this Packet Tracer.
Packet Tracer—Troubleshooting Challenge—Document the Network (37.2.13)
In this Packet Tracer activity, you will document a network that is unknown to you.
- Test network connectivity.
- Compile host addressing information.
- Remotely access default gateway devices.
- Document default gateway device configurations.
- Discover devices on the network.
- Draw the network topology.
Refer to the online course to complete this Packet Tracer.
Help Desks (37.3)
A help desk is typically the first line of support in any organization. This section discusses the structure, operations, and skills needed for an affective help desk organization.
The Security Policy (37.3.1)
Organizations operate with well-defined corporate, employee, and security policies.
The “Security Policy” document contains policies that inform users, IT staff, and managers of the requirements for protecting technology and information assets. As shown Figure 37-23, there are policies for:
- Specifying how users are identified and authenticated
- Setting password length, complexity, and refresh interval
- Defining what behavior is acceptable on the corporate network
- Specifying remote access requirements, etc.
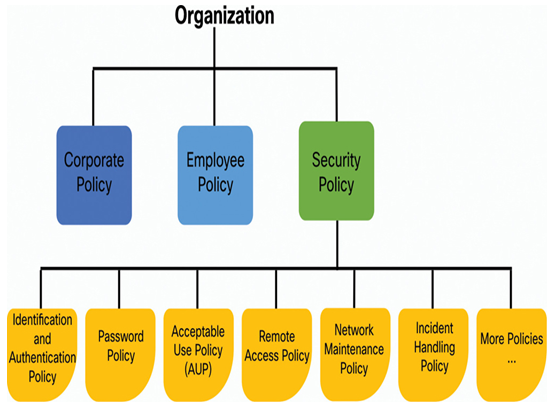
Figure 37-23 Example of How Security Documentation Fits In with the Larger Organizational Policies
The Security Policy document is a constantly evolving document that reacts to changes in the threat landscape, new vulnerabilities, and business and employee requirements. The Security Policy helps the IT team understand what they must do to keep the network operational and secure by using:
- Standard operating procedures (SOPs)—These define step-by-step actions that must be completed for any given task to comply with a policy. There are SOPs to follow when replacing network devices, installing (or uninstalling) applications, onboarding new employees, terminating existing employees, and more.
- Guidelines—These cover the areas where there are no SOPs defined.
When users encounter a problem or need network support, they must contact a “help desk.” The help desk assists users by following the defined SOPs and guidelines. The help desk will use a ticketing system to manage the steps within the troubleshooting life cycle shown in Figure 37-24.
This section will focus on using a ticketing system to complete the first three steps shown in Figure 37-24.
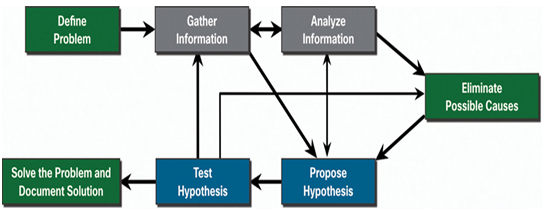
Figure 37-24 Seven-Step Troubleshooting Process
A help desk is a specialized team in an IT department that is the central point of contact for employees or customers.
When users require support, they must contact the IT help desk. This may be done by using an online reporting tool, live chat, telephone, or email (e.g., [email protected]). Help desks often use a “shared” email account. This means that all help desk technicians can see the email requests and respond to them accordingly.
Note
The online reporting tool could be integrated into the ticketing system.
Often, the help desk technician may be able to quickly answer or solve user issues. For example, if an organization had an Internet network failure, users may contact the help desk asking why they cannot reach external sites. The technician would inform them that the network is down, and that it should be operational within a specific time.
However, if the request for support is valid, then the technician will create a “trouble ticket.” This is done using special ticketing system software to manage requests, incidents, and reported problems. These “tickets” can be created by the user using a ticketing system dashboard or by a help desk technician. Typically, a user initiates the ticket, and the help desk technician validates it.
The help desk technician may have to gather additional information about the request. When questioning users, use effective questioning techniques and listen carefully to the user answers. You may also have to physically investigate the device or connect remotely to replicate the problem, execute commands, and check configurations.
The technician would then analyze the collected data and either:
- Solve the problem—Once the user problem has been addressed, the technician would update and close the trouble ticket. Updating the ticket solution is important because it can populate the ticketing system database. Therefore, if the same problem is reported by another user, the responding technician can search the database to quickly resolve the problem. In addition, administrators can analyze the tickets to identify common issues and their causes in order to globally eliminate the problem, if possible.
- Escalate the trouble ticket—Some problems are more complex or require access to devices which the technician has no credentials for. In these cases, the technician must escalate (i.e., forward) the trouble ticket to a more experienced technician. It is important that all documentation captured from the user is clear, concise, and accurate.
Figure 37-25 summarizes a typical trouble ticket process that a help desk technician would have to perform.
Note
Processes can vary depending on the organization.
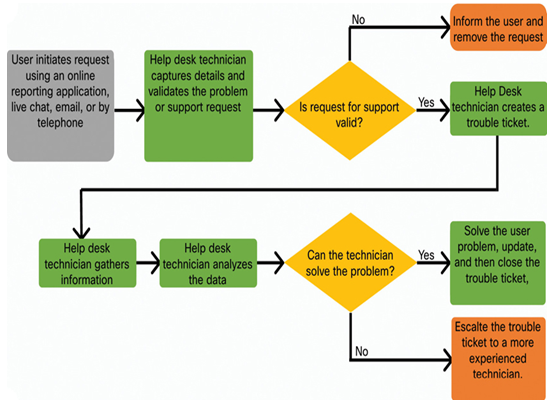
Figure 37-25 Typical Trouble Ticket Process
