After a Telnet connection is established, users can perform any authorized function on the server, just as if they were using a command line session on the server itself. If authorized, they can start and stop processes, configure the device, and even shut down the system.
Although the Telnet protocol can require a user to login, it does not support transporting encrypted data. All data exchanged during Telnet sessions is transported as plaintext across the network. This means that the data can be easily intercepted and understood.
The Secure Shell (SSH) protocol offers an alternate and secure method for server access. SSH provides the structure for secure remote login and other secure network services. It also provides stronger authentication than Telnet and supports transporting session data using encryption. As a best practice, network professionals should always use SSH in place of Telnet, whenever possible.
Figure 16-8 illustrates how SSH is more secure than Telnet. Notice how the data captured by the hacker when Telnet is used is clearly readable while the data captured when SSH is used is encrypted and therefore more secure.
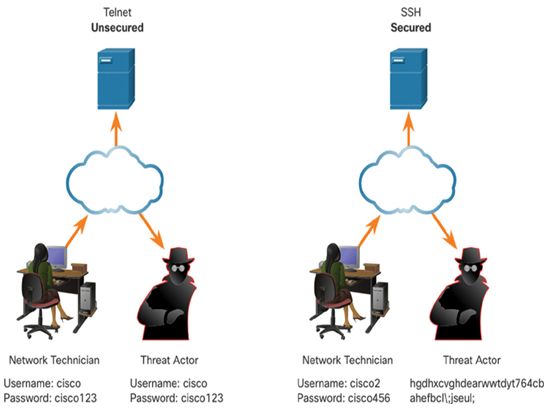
Figure 16-8 Telnet and SSH Comparison
Packet Tracer – Use Telnet and SSH (16.6.4)
In this activity, you will establish remote session to a router using Telnet and SSH.
Refer to the online course to complete this Packet Tracer.
Email is one of the most popular client/server applications on the internet. Email servers run server software that enables them to interact with clients and with other email servers over the network.
Email Clients and Servers (16.7.1)
Email is one of the most popular client/server applications on the internet. Email servers run server software that enables them to interact with clients and with other email servers over the network.
Each mail server receives and stores mail for users who have mailboxes configured on the mail server. Each user with a mailbox must then use an email client to access the mail server and read these messages. Many internet messaging systems use a web-based client to access email. Examples of this type of client include Microsoft 365, Yahoo, and Gmail.
Mailboxes are identified by the format: [email protected]
Various application protocols used in processing email include SMTP, POP3, and IMAP4, as shown in Figure 16-9.
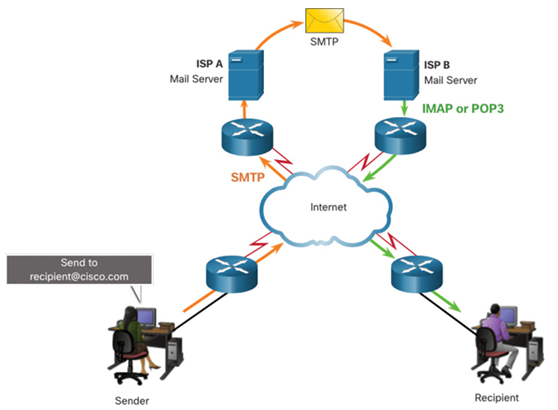
Figure 16-9 SMTP, POP3, and IMAP4 Mail Protocols in Operation
Simple Mail Transfer Protocol (SMTP)
SMTP is used by an email client to send messages to its local email server. The local server then decides if the message is destined for a local mailbox or if the message is addressed to a mailbox on another server.
If the server has to send the message to a different server, SMTP is used between those two servers as well. SMTP requests are sent to port 25.
Figure 16-10 shows how SMTP is used to send email.
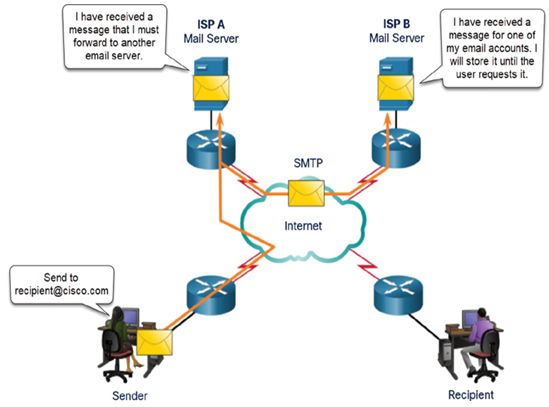
Figure 16-10 SMTP Operation
A server that supports POP clients receives and stores messages addressed to its users. When the client connects to the email server, the messages are downloaded to the client. By default, messages are not kept on the server after they have been accessed by the client. Clients contact POP3 servers on port 110.
Internet Message Access Protocol (IMAP4)
A server that supports IMAP clients also receives and stores messages addressed to its users. However, unlike POP, IMAP keeps the messages in the mailboxes on the server, unless they are deleted by the user. The most current version of IMAP is IMAP4 which listens for client requests on port 143.
Many different email servers exist for the various network operating system platforms.
