What happens when the switch receives a frame addressed to a new host that is not yet in the MAC address table? If the destination MAC address is not in the table, the switch does not have the necessary information to create an individual circuit. When the switch cannot determine where the destination host is located, it uses a process called flooding to forward the message out to all attached hosts except for the sending host. Each host compares the destination MAC address in the message to its own MAC address, but only the host with the correct destination address processes the message and responds to the sender.
How does the MAC address of a new host get into the MAC address table? A switch builds the MAC address table by examining the source MAC address of each frame that is sent between hosts. When a new host sends a message or responds to a flooded message, the switch immediately learns its MAC address and the port to which it is connected. The table is dynamically updated each time a new source MAC address is read by the switch. In this way, a switch quickly learns the MAC addresses of all attached hosts.
Figure 7-7 through 7-10 demonstrate this operation.
In Figure 7-7, Source PC H3 is sending data to Destination PC H7. The switch does not yet have a MAC address for H7.
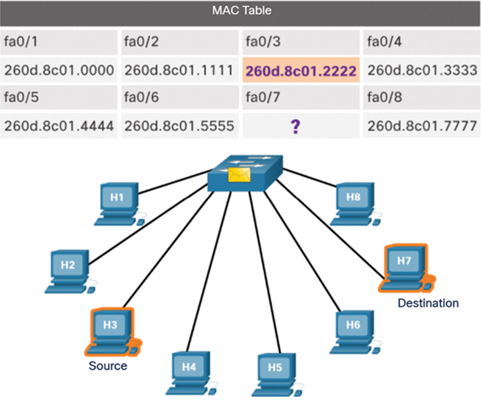
Figure 7-7 Source sends a Message to the Destination
In Figure 7-8, the switch floods the frame received from H3 out every other port.
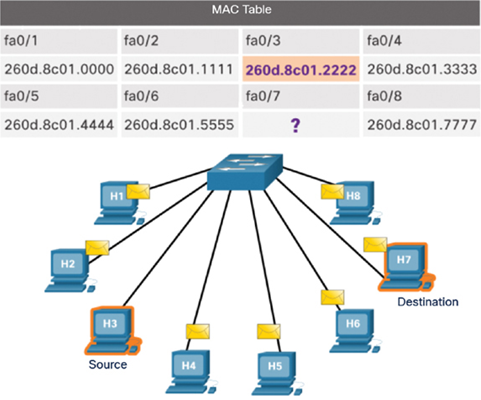
Figure 7-8 Switch Floods the Message
In Figure 7-9, after H7 receives the frame, the IP address of the encapsulated packet matches H7’s IP address. Therefore, H7 replies to H3.
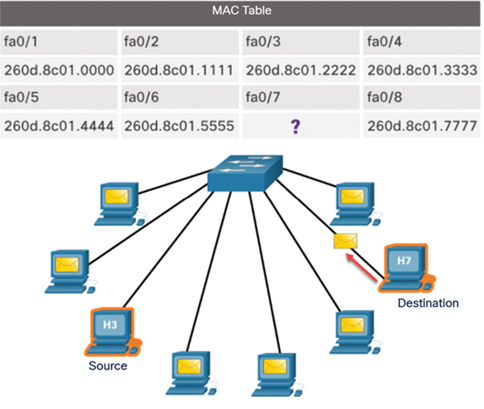
Figure 7-9 The Destination Replies to the Message
In Figure 7-10, the switch updates its table with the MAC address for H7 to map the MAC address to the port.
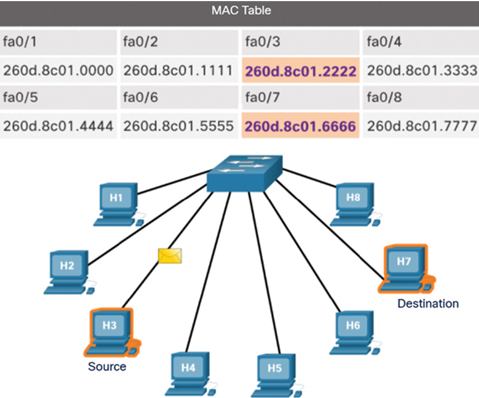
Figure 7-10 The Switch Records the MAC Address for the Destination
The Access Layer Summary (7.3)
The following is a summary of each topic in the chapter and some questions for your reflection.
What Did I Learn in this Module? (7.3.1)
• Encapsulation and the Ethernet Frame—The process of placing one message format inside another message format is called encapsulation. De-encapsulation occurs when the process is reversed by the recipient and the letter is removed from the envelope. Just as a letter is encapsulated in an envelope for delivery, so computer messages are encapsulated. A message that is sent over a computer network follows specific format rules for it to be delivered and processed.
The Ethernet protocol standards define many aspects of network communication including frame format, frame size, timing, and encoding. The format for Ethernet frames specifies the location of the destination and source MAC addresses, and additional information including preamble for sequencing and timing, start of frame delimiter, length and type of frame, and frame check sequence to detect transmission errors.
• The Access Layer—The access layer is the part of the network in which people gain access to other hosts and to shared files and printers. The access layer provides the first line of networking devices that connect hosts to the wired Ethernet network. Within an Ethernet network, each host can connect directly to an access layer networking device using an Ethernet cable. Ethernet hubs contain multiple ports that are used to connect hosts to the network. Only one message can be sent through an Ethernet hub at a time. Two or more messages sent at the same time will cause a collision. Because excessive retransmissions can clog up the network and slow down network traffic, hubs are now considered obsolete and have been replaced by Ethernet switches.
An Ethernet switch is a device that is used at Layer 2. When a host sends a message to another host connected to the same switched network, the switch accepts and decodes the frames to read the MAC address portion of the message. A table on the switch, called a MAC address table, contains a list of all the active ports and the host MAC addresses that are attached to them. When a message is sent between hosts, the switch checks to see if the destination MAC address is in the table. If it is, the switch builds a temporary connection, called a circuit, between the source and destination ports. Ethernet switches also allow for sending and receiving frames over the same Ethernet cable simultaneously. This improves the performance of the network by eliminating collisions.
A switch builds the MAC address table by examining the source MAC address of each frame that is sent between hosts. When a new host sends a message or responds to a flooded message, the switch immediately learns its MAC address and the port to which it is connected. The table is dynamically updated each time a new source MAC address is read by the switch.
There is a lot going on behind the scenes when I send an email to a friend. Way more than I knew about! Data gets encapsulated when I send an email and then it’s de-encapsulated when my friend opens that email. The access layer of the OSI model is where all of this happens. Now that you know about encapsulation and the access layer, what else do you do on your computer, tablet, or smartphone that requires encapsulation and the protocols used at the access layer?
