Although ping is the most commonly used network troubleshooting command, there are other useful commands that are available on Windows devices.
The ping command can verify end-to-end connectivity. However, if a problem exists and the device cannot ping the destination, the ping command does not indicate where the connection was really dropped. To pinpoint this, another command known as traceroute or tracert must be used. Microsoft Windows uses the tracert command, while other operating systems commonly use the command traceroute.
The tracert utility provides connectivity information about the path a packet takes to reach the destination and about every router (hop) along the way. It also indicates how long a packet takes to get from the source to each hop and back (round-trip time). The tracert utility can help identify where a packet may have been lost or delayed due to bottlenecks or slowdowns in the network.
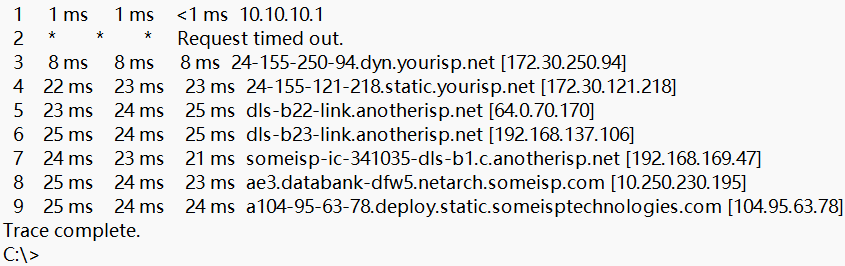
In Example 36-2, the user is tracing the path to Cisco. The path is unique to this user. Your path will have a different listing of hops and may be shorter or longer (number of hops).
Note
Notice in the output that the second hop failed. This is most likely due to a firewall configuration on that device which does not permit responding to packets from the tracert command. However, the device does forward the packets to the next hop.
Example 36-2 Tracing a Route to Cisco
C:>
tracert www.cisco.com
Tracing route to e2867.dsca.someispedge.net [104.95.63.78]
over a maximum of 30 hops:
The basic tracert command will only allow up to 30 hops between a source and destination device before it assumes that the destination is unreachable. This number is adjustable by using the -h parameter. Other modifiers, displayed as options in Example 36-3, are also available.
Example 36-3 The Options for the tracert Command
C:>
tracert
Usage: tracert [-d] [-h maximum_hops] [-j host-list] [-w timeout]
[-R] [-S srcaddr] [-4] [-6] target_name
Options:
-d Do not resolve addresses to hostnames.
-h maximum_hops Maximum number of hops to search for target.
-j host-list Loose source route along host-list (IPv4-only).
-w timeout Wait timeout milliseconds for each reply.
-R Trace round-trip path (IPv6-only).
-S srcaddr Source address to use (IPv6-only).
-4 Force using IPv4.
-6 Force using IPv6.
C:>
Sometimes it is necessary to know which active TCP connections are open and running on a networked host. The netstat command is an important network utility that can be used to verify those connections. As shown in Example 36-4, the netstat command lists the protocol in use, the local address and port number, the foreign address and port number, and the state of the connection.
Example 36-4 The netstat Command
C:>
netstat
Active Connections
Proto Local Address Foreign Address State
TCP 10.10.10.130:58520 dfw28s01-in-f14:https ESTABLISHED
TCP 10.10.10.130:58522 dfw25s25-in-f14:https ESTABLISHED
TCP 10.10.10.130:58523 dfw25s25-in-f14:https ESTABLISHED
TCP 10.10.10.130:58525 ec2-3-13-132-189:https ESTABLISHED
TCP 10.10.10.130:58579 203.104.160.12:https ESTABLISHED
TCP 10.10.10.130:58580 104.16.249.249:https ESTABLISHED
TCP 10.10.10.130:58624 52.242.211.89:https ESTABLISHED
TCP 10.10.10.130:58628 24-155-92-110:https ESTABLISHED
TCP 10.10.10.130:58651 ec2-18-211-133-65:https ESTABLISHED
TCP 10.10.10.130:58686 do-33:https ESTABLISHED
TCP 10.10.10.130:58720 172.253.119.189:https ESTABLISHED
TCP 10.10.10.130:58751 ec2-35-170-0-145:https ESTABLISHED
TCP 10.10.10.130:58753 ec2-44-224-80-214:https ESTABLISHED
TCP 10.10.10.130:58755 a23-65-237-228:https ESTABLISHED
C:>
Unexplained TCP connections can pose a major security threat. This is because they can indicate that something or someone is connected to the local host. Additionally, unnecessary TCP connections can consume valuable system resources, thus slowing down the performance of the host. Netstat should be used to examine the open connections on a host when performance appears to be compromised.
Many useful options are available for the netstat command. These options can be viewed by typing netstat /? at the command prompt, as shown in Example 36-5.
Example 36-5 Options for the netstat Command
C:>
netstat /?
Displays protocol statistics and current TCP/IP network connections.
NETSTAT [-a] [-b] [-e] [-f] [-n] [-o] [-p proto] [-r] [-s] [-t] [-x] [-y] [interval]
-a Displays all connections and listening ports.
-b Displays the executable involved in creating each connection or
listening port. In some cases well-known executables host
multiple independent components, and in these cases the
sequence of components involved in creating the connection
or listening port is displayed. In this case the executable
name is in [] at the bottom, on top is the component it called,
and so forth until TCP/IP was reached. Note that this option
can be time-consuming and will fail unless you have sufficient
permissions.
-e Displays Ethernet statistics. This may be combined with the -s
option.
-f Displays Fully Qualified Domain Names (FQDN) for foreign
addresses.
-n Displays addresses and port numbers in numerical form.
-o Displays the owning process ID associated with each connection.
-p proto Shows connections for the protocol specified by proto; proto
may be any of: TCP, UDP, TCPv6, or UDPv6. If used with the -s
option to display per-protocol statistics, proto may be any of:
IP, IPv6, ICMP, ICMPv6, TCP, TCPv6, UDP, or UDPv6.
-q Displays all connections, listening ports, and bound
nonlistening TCP ports. Bound nonlistening ports may or may not
be associated with an active connection.
-r Displays the routing table.
-s Displays per-protocol statistics. By default, statistics are
shown for IP, IPv6, ICMP, ICMPv6, TCP, TCPv6, UDP, and UDPv6;
the -p option may be used to specify a subset of the default.
-t Displays the current connection offload state.
-x Displays NetworkDirect connections, listeners, and shared
endpoints.
-y Displays the TCP connection template for all connections.
Cannot be combined with the other options.
interval Redisplays selected statistics, pausing interval seconds
between each display. Press CTRL+C to stop redisplaying
statistics. If omitted, netstat will print the current
configuration information once.
C:>
