User-defined routes
In some cases, you will want to configure the routing of packets differently from what is pro- vided by the default system routes. One of these scenarios is when you want to send traffic through a network virtual appliance, such as a third-party load balancer, firewall, or router deployed into your VNet from the Azure Marketplace.
To make this possible, create what are known as user-defined routes (UDRs). The UDR is implemented by creating a route table resource. Within the route table, a number of routes are configured. Each route specifies the destination IP range (in CIDR notation) and the next hop IP address. A variety of different types of next hop are supported:
- Virtual appliance A virtual machine running a network application such as a load balancer or firewall. With this next hop type, you also specify the IP address of the appliance, which can be a virtual machine or internal load balancer for high-availability virtual appliances.
- Virtual network gateway Used to route traffic to a VPN gateway (but not an ExpressRoute gateway, which uses BGP for custom routes). Because there can be only one VPN gateway associated with a VNet, you are not prompted to specify the actual gateway resource.
- Virtual network Used to route traffic within the VNet.
- Internet Used to route a specific IP address or prefix to the internet.
- None Used to drop all traffic sent to a given IP address or prefix.
This route table is then associated with one or more subnets. Traffic originating in the subnet whose destination matches the destination IP range of a route table rule will instead be routed to the corresponding next hop IP address. The service running at this IP address is responsible for all onward routing.

Figure 4-12 shows a UDR that has been created to direct outbound traffic via a virtual appliance. In this case, the appliance is a firewall running as a VM in Azure in the DMZ subnet.
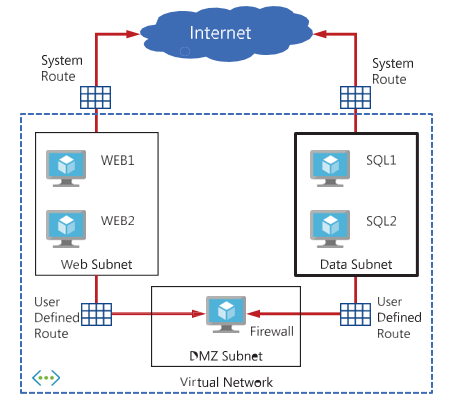
FIGURE 4-12 N-Tier application deployed with a firewall using user-defined routes
The same appliance can also be used to filter traffic between the Apps and Data subnets.
An example route table implementing this design is shown in Figure 4-13.
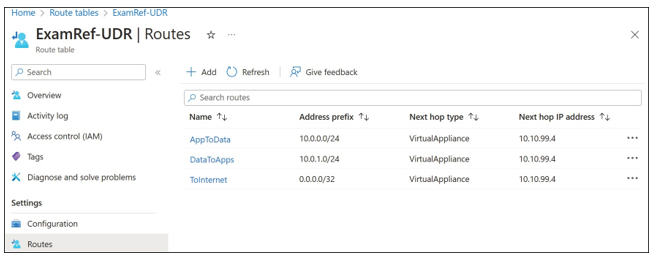
FIGURE 4-13 Route table rules forcing network traffic through a firewall

