You can create accounts for each user to be managed by Cloud Identity manually in the Users tab in the Directory section of the Google Admin console by selecting Add new user as shown in Figure 12.7. Alternatively, you can upload user accounts via a CSV file, sync users with your existing LDAP directory, such as Active Directory, or use the Admin SDK Directory API to create and manage users programmatically.
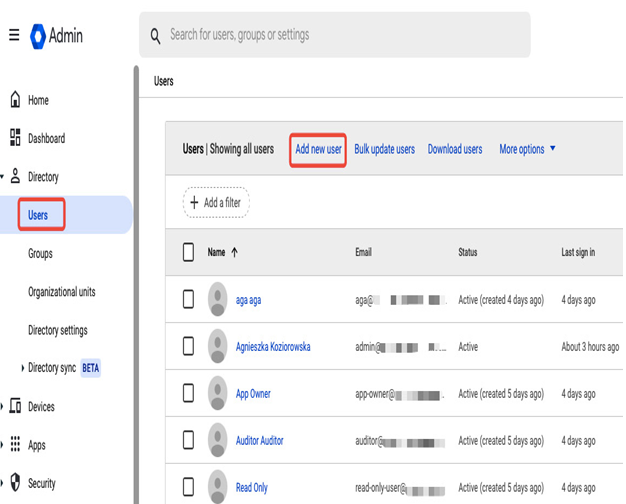
Figure 12.7 – Adding users in the Google Admin console
Next, you can create groups and add users to groups in the Groups section. For example, as presented in the following screenshot, one of the first groups that should be created is the gcp-organization-admins group (the name is only a suggestion), which consists of users that, in the next step, obtain permissions to create and manage a Google Cloud organization, a root node in the Google Cloud resource hierarchy:
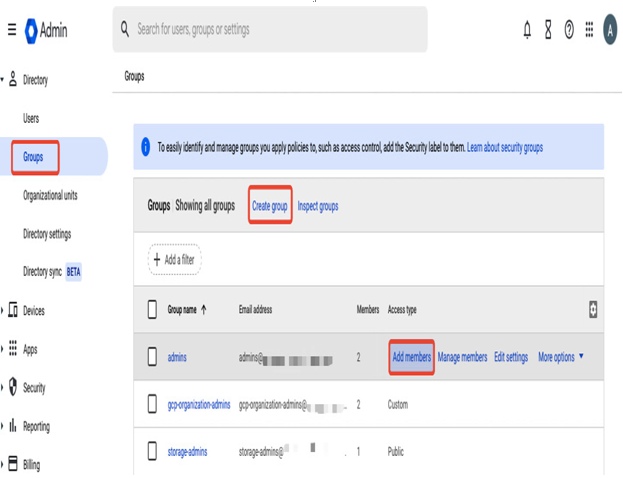
Figure 12.8 – Groups in the Google Admin console
The necessary permissions to manage an organization in Google Cloud are not set in the Google Admin console but in the Google Cloud console. Users with Cloud Identity accounts will be able to log in to the Google Cloud console and create and access resources according to their assigned roles and permissions. The following section will provide more details on managing an organization, users, and resources.
Note that although in Google Console, you can’t create individual users, there is still an option to create service accounts and Google groups. Permissions in Google Cloud can be granted to a Cloud Identity user, a Cloud Identity group, a Google Cloud service account, and a Google group. Find out more about Google Groups at https://cloud.google.com/iam/docs/groups-in-cloud-console.
Identity and Access Management (IAM)
When you log in to the Google Cloud console with a newly created super admin user, right after its Cloud Identity is configured, a Google Cloud organization resource will be automatically created once you accept the terms and conditions. In addition, the organization will be linked to your billing.
As a first step after logging in as a super admin, you should go to the IAM section of IAM & Admin and assign the Organization Administrator role to the previously created gcp-organization-admins group, as shown in the following screenshot. Next, you can log in as a member of this group, start configuring resources, and provide other users with permissions. This way, you will avoid using a super admin account to manage Google Cloud resources. The role and permissions assignment process will be explained in detail in the following sections.
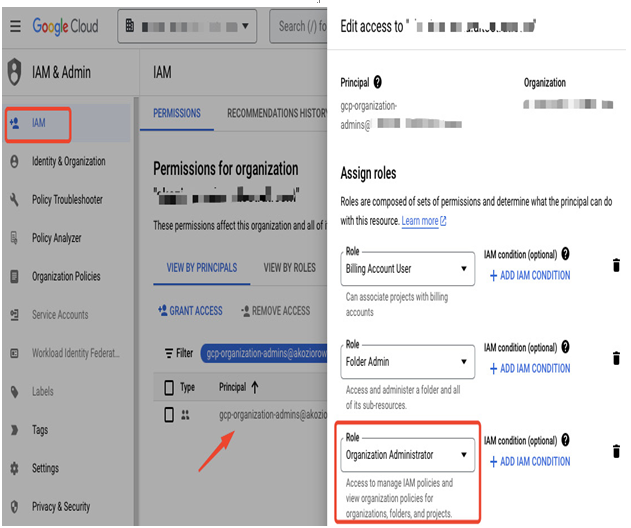
Figure 12.9 – Assigning the Organization Administrator role to the gcp-organization-admins group
Identity and Access Management (IAM) is where you centrally control who can do what type of activities on which Google Cloud resources. Note that resources are not only Google Cloud services such as Compute Engine VMs or Google Cloud Storage. IAM can control access to a project, folder, or even organizational level. It helps to adopt the security principle of least privilege as it allows building fine-grained access to resources. Let’s investigate a hierarchy of Google Cloud resources to better understand how permissions are applied across all levels.
