Virtual network service endpoints
In some scenarios, a storage account is only accessed from within an Azure virtual network.
In this case, it is desirable from a security standpoint to block all internet access. Configuring virtual network service endpoints for your Azure storage account, you can remove access from the public internet and only allow traffic from a virtual network for improved security.
Another benefit of using service endpoints is optimized routing. Service endpoints create a direct network route from the virtual network to the storage service. If forced tunneling is being used to force internet traffic to your on-premises network or to another network appliance, requests to Azure Storage will follow that same route. By using service endpoints, you can use a direct route to the storage account instead of the on-premises route, so no additional latency is incurred.
Configuring service endpoints requires two steps. First, to update the subnet settings, you should choose your virtual network from the Virtual Networks blade. Then select Subnets on the left under Settings. Click the subnet you plan to configure to access the subnet settings. After selecting the desired subnet, under Service Endpoints, choose Microsoft.Storage from the Services drop-down menu. This creates the route from the subnet to the storage service but does not restrict which storage account the virtual network can use. Figure 2-7 shows the subnet settings, including the service endpoint configuration.

FIGURE 2-7 Configuring a subnet with a service endpoint for Azure Storage
The second step is to configure which virtual networks can access a particular storage account. From the storage account blade, click Networking. Under Public Network Access, click Enabled From Selected Virtual Networks And IP Addresses to reveal the Firewall and Virtual Network settings, as shown previously in Figure 2-1. Under Virtual Networks, select Add Exist- ing Virtual Network to add the virtual networks and subnets that should have access to this storage account.
Blob Storage access levels
Storage accounts support an additional access control mechanism that is limited only to Blob Storage. By default, no public read access is enabled for anonymous users, and only users with rights granted through RBAC or with the storage account name and key will have access to the stored blobs. To enable anonymous user access, you must enable Allow Blob Anonymous Access (shown in Figure 2-8) and configure the container access level (shown in Figure 2-9).
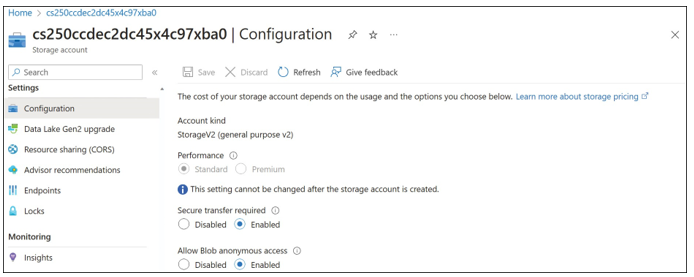
FIGURE 2-8 Storage account configuration
The anonymous access level for a container can be specified during creation, or modified after it has been created. The supported levels of blob containers are as follows:
- Private Only principals with permissions can access the container and its blobs. Anonymous access is denied.
- Blob Only blobs within the container can be accessed anonymously.
- Container Blobs and their containers can be accessed anonymously.
You can change the access level through the Azure portal, Azure PowerShell, Azure CLI, programmatically using the REST API, or by using Azure Storage Explorer. The access level is configured separately on each blob container.

FIGURE 2-9 Blob Storage access levels
A shared access signature token (SAS token) is a URI query string parameter that grants access to containers, blobs, queues, and/or tables. Use a SAS token to grant access to a client or service that should not have access to the entire contents of the storage account (and there- fore, should not have access to the storage account keys) but still requires secure authentica- tion. By distributing a SAS URI to these clients, you can grant them access to a specific resource, for a specified period of time, and with a specified set of permissions. SAS tokens are com- monly used to read and write the data to users’ storage accounts. Also, SAS tokens are widely used to copy blobs or files to another storage account.